Perpetrators of CWT ransomware attack recommend password rotation, admin rights removal, and application control as tips to prevent attacks.
Even in movies, we don’t get to see burglars giving tips on how to protect our homes. In the cybersecurity world, the modus operandi and the measures to prevent attacks mostly revolve around assumptions. Last week, in a rare happening, Jack Stubbs, the European cybersecurity correspondent at Reuters has published the online chat room negotiations that reportedly took place between a victim of a ransomware attack and the attack perpetrators.
The best part of the story is the tips given by the attackers to prevent attacks after the ransom was paid. The tips lay stress on passwords protection, locking down administrator rights, and establishing application control - which security experts have long been recommending.
For the uninitiated
Last week, CWT, the US-based business travel management firm faced a ransomware attack. Cybercriminals stole reams of sensitive corporate files and claimed they had knocked 30,000 computers offline. The attackers used a strain of ransomware called Ragnar Locker, which encrypts computer files and renders them unusable until the victim pays for access to be restored. The firm reportedly paid $4.5 million to the hackers.
Reuters got access to a public chat room conversation reportedly between the CWT representative and the hacker group. At the end of the negotiations, after the ransom was paid, the hackers have given a set of security recommendations to prevent future attacks.
Key recommendations
The cybercriminals have given a list of recommendations to prevent ransomware attacks. Some of the key recommendations include:
- Anti-virus solutions are needed, but they alone are not effective
- Change passwords every month
- Check the privileges of users. Ensure that users have only the absolutely needed rights
- Grant permission to run the approved applications only
- Force end administrator sessions
- Install endpoint detection and response (EDR) tools

The above recommendations clearly bring out the importance of the foundational security measures that security experts have been stressing for so long.
Admin privileges and Malware/Ransomware propagation
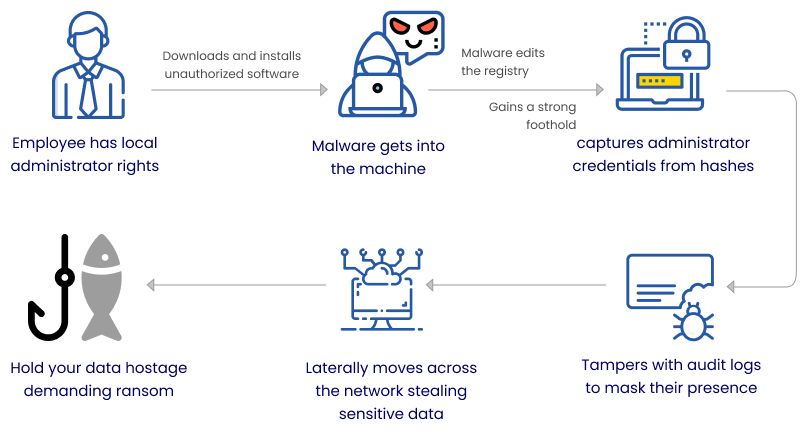
Malware quickly and easily spreads through the installation of unapproved software, pirated tools, opening malicious email attachments, clicking malicious URLs, visiting harmful pages (drive-by downloads), and so on. Even tech-savvy end-users can unintentionally fall prey to any of these attacks and malware would gain a strong foothold.
Most of these attacks happen mainly because end-users possess local administrator rights. When your employees work from home, quite unintentionally, they tend to do all these.
After getting on to a computer, the malware goes about editing the registry gaining a strong foothold, captures credentials, tampers audit logs, and moves laterally across the network stealing sensitive data.
Organizations should have control over what applications their end-users are installing on corporate laptops while working remotely. Preventing the usage of unauthorized applications reduces the risk of Malware.
The best practice approach
The best practice approach to prevent attacks is to enforce least privileges across the organization by removing local administrator rights from all endpoints. But this could lead to productivity issues and frustration as employees will have to approach the system administration team even for trivial needs.
To avoid that, administrator rights removal should be combined with robust application control. Define and control which applications can be run by standard users. Whitelist trusted applications and prevent unapproved and malicious applications. This empowers standard users to seamlessly run approved applications (that would normally require admin rights) whenever needed. When specific users require broader privilege, you can grant a time-limited, fully controlled, and comprehensively audited temporary administrator access on a need basis. This is controlled by a well-defined workflow, which takes care of automatically revoking the access.
Another best practice measure, which is often overlooked is periodic password resets. If the passwords of sensitive IT assets are changed periodically and assigned with strong, unique passwords, the risk of cyber attacks could be reduced.
How does Securden help?
Securden helps you thwart security issues with an extremely easy-to-use, simple to deploy, and a highly affordable privileged access security solutions.
- Securden Endpoint Privilege Manager helps you to remove administrator privileges on endpoints and control application usage without impacting productivity. It seamlessly elevates applications for standard users. Through robust workflows and policy-based controls, end-user experience remains the same even when administrator rights are removed.
- Securden Privileged Account Manager (PAM) helps in protecting passwords, enforcing password management best practices, and in controlling privileged access. You can ensure a fully controlled and completely monitored just-in-time and just-enough access to the IT infrastructure. Securden PAM also helps in enforcing least privilege, application and command controls on servers.
Schedule a demo or start a 30-day trial now.
































![What is Cloud PAM? [Definition, Features, Benefits, and Factors to Choose the Right One]](/images/cloud-pam/cloud-pam-blog-image.webp)




























