With the easy availability of billions of compromised credentials on the dark web, and the practice of password reuse rampant, hackers have a heyday. The password-based attack on the fuel pipeline giant underscores the urgent need for constantly checking corporate passwords against the compromised credentials database besides concentrating on basic security measures.
Perpetrating a cyberattack nowadays looks like a child’s play, literally. As organizations continue to fail to pay attention to the very basics of IT security (all the while investing heavily on advanced security measures), it doesn’t require sophisticated skills or specialized knowledge to carry out an attack successfully. Billions of passwords exposed during various cyberattacks are freely available on the dark web, and cybercriminals are merrily obtaining username-password combinations to hold a company to ransom and mint millions of dollars.
In the case of the recent high-profile attack on the Colonial pipeline in the United States, various reports suggest that hackers have used the easiest possible technique - obtaining username and password (probably from the dark web) - to gain remote access to the fuel pipeline giant’s network and plant ransomware. The company reportedly paid $4.4 million in ransom.
Colonial Pipeline in the United States operates a fuel pipeline that carries about 100 million gallons of gasoline, diesel fuel, jet fuel, and natural gas along a 5,500-mile path from Texas to New Jersey. On May 7, 2021, one of the technicians manning the control room noticed a ransomware note on a system screen demanding ransom in cryptocurrency. The hackers had apparently stolen about 100 GB of information.
The company had to immediately shut down the pipeline as a precautionary measure, which led to a crippling effect on the chain. Long lines were seen at gas stations, many ran out of stock, and fuel prices started increasing as people resorted to panic buying.
The company commenced an exhaustive examination of the pipeline on a war footing to see if there was any damage to the pipeline. It tracked 29,000 miles on the ground and through the air and finally found that the pipeline wasn’t damaged and resumed its operations on May 12.
While this was going on, the company reportedly paid $4.4 million to the cybercriminals to restore its systems. In a recent development, it is reported that the Department of Justice has recovered a major portion of the ransom paid to the hackers. Heartening news, indeed.
Compromised credentials grant access to the oil kingdom
Though details about the exact cause for the attack are still emerging and investigations are going on, reports quoting FireEye, the cybersecurity firm that is assisting Colonial Pipeline in its investigation and recovery efforts, state that the attack happened due to a compromised password. The password granted access to a VPN account that was active but not in use. The account didn't mandate a second authentication factor.
It should have been literally a cakewalk for hackers.
At the moment, it is not clear how the attackers obtained the compromised credentials. Many researchers suggest that they would have probably obtained it from the compromised credentials database available on the dark web. An employee might have used the same password for the VPN account too.
It is estimated that it will take several months for the organization to recover from the attack fully.
Stolen credentials and cyberattacks - an everyday affair
Ransomware attacks and other forms of cyberattacks have become an everyday affair now. Until a few years ago, the hackers targeted primarily the banking and financial institutions. Now, businesses of all types and sizes ranging from dental clinics, meat vendors, supermarkets, hospitals, educational institutions to online surveillance systems, public utility services, industrial control systems, government organizations, manufacturing companies, and other enterprises are all constantly facing attacks.
The involvement of stolen credentials and misuse of administrative access are increasingly reported in most of the attacks.
As we have been stressing time and again, cybercriminals are always on the lookout for administrative credentials. Often, attackers don’t actually hack into networks; they simply royally walk in using stolen, weak, or compromised credentials freely available on the dark web. They follow a few other simple techniques, such as phishing emails to deliver malware and gain a foothold on machines. Known vulnerabilities that remain unpatched make their job easy. They then capture administrative credentials from hashes or through keystroke loggers and move across the network and finally perpetrate the attack by exploiting privileged access.
The dark web is full of stolen passwords
As a result of the continuing credential spill incidents, a total of 3.2 Billion breached credentials (username and password combinations) are freely available on the web today. Anyone can access them. Still worse, the database continues to accumulate new passwords as credential spills continue to happen unabated.
Password reuse by employees - a significant causative factor for attacks
Reusing the same passwords across multiple IT assets and applications is a recipe for disaster. Yet, this practice goes unchecked in many organizations. It is pretty common to see the same passwords assigned to multiple IT assets; developers reusing passwords across their personal and work accounts; passwords on spreadsheets circulated across departments; a departing IT staff exiting with a copy of all the credentials, and similar practices.
When developers reuse passwords, a compromise of one of their personal accounts gives hackers easy access to corporate data. Many business establishments face cyberattacks simply due to the password reuse practices of their employees. Hackers use the credentials to gain unauthorized access to various networks.
Checking for the use of compromised credentials is a must
Credential stuffing has now emerged as a significant threat. IT divisions should continuously check if any of the passwords assigned for their resources already finds a place in the compromised credentials database. Since employee activities are involved in assigning passwords, such a check should be a continuous process.
Mostly, users are not aware when their passwords are exposed in credential spilling attacks. As explained above, if a breached password is being used, it may lead to a spate of cyberattacks.
Manual approaches to checking passwords against compromised credentials database are both time-consuming and error-prone. You can use products like Securden Password Vault for Enterprises or Securden Unified PAM that proactively periodically scan the compromised credentials database and check if any of the passwords stored in the product matches with the passwords that have been exposed in known data breaches. Securden continuously monitors this and provides timely alerts and informative reports that help in preventing attacks.
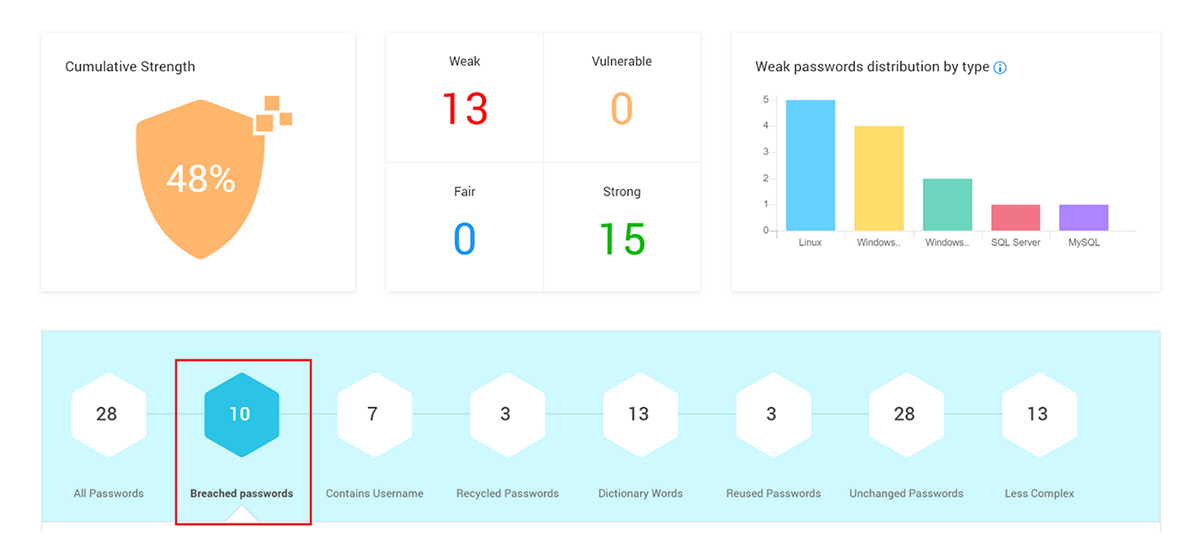
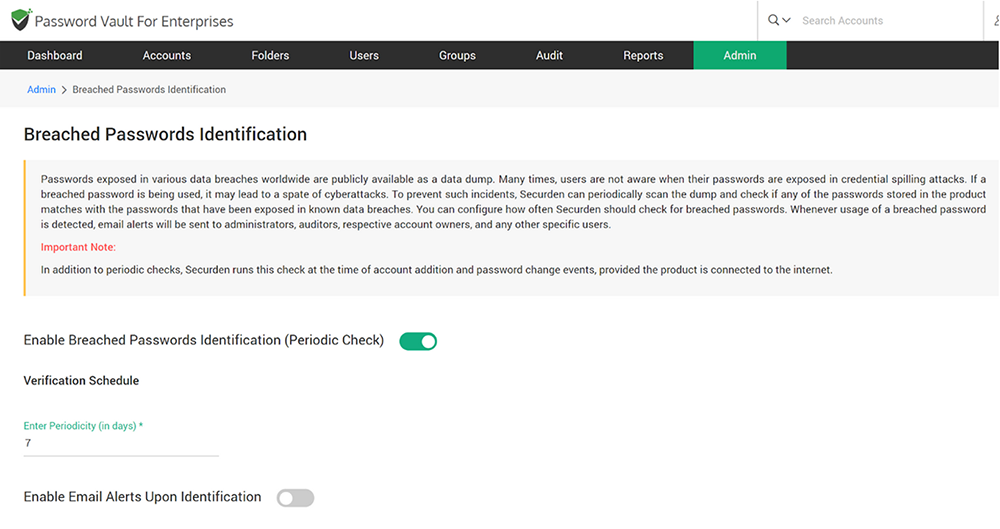
Fundamental security aspects shouldn’t be ignored
Many organizations concentrate on deploying sophisticated and advanced security arsenal but lose sight of the fundamental measures. While advanced security measures certainly help protect the organization, holes in the foundational elements become a cakewalk for hackers.
Some of the most neglected security fundamentals include:
- Password security best practices
- Multi-factor Authentication enforcement
- IT access controls
- Timely patching to fix known vulnerabilities
The lack of these measures has led to some of the worst data breaches in recent times. Of these, poor password hygiene is perhaps the most notorious factor.
Basic security controls are not to be exempted
In some organizations, when IT divisions enforce certain basic practices, end users come up with exemption requests or find ways to circumvent the process. Citing work priorities, users raise requests for relaxation when passwords are to be changed, when MFA takes force, when maintenance is due, when a monitoring system needs to be deployed, or when a scan is to be done. These practices are equal to having no controls at all and might land organizations in big trouble.
Password security hygiene requires special attention
It is evident that ignoring the fundamental principles of password security often lands organizations in trouble. To avoid becoming a victim of password-based attacks, companies should pay special attention to basic password security hygiene and enforce password management best practices at all levels:
Check password reuse
Users should be warned about the perils of reusing the same password across multiple accounts. Passwords used on personal accounts should never be used on any of the corporate accounts.
Strong, unique passwords
Every single corporate login account should have a strong, unique password. The most common weak passwords like ‘password123’, ‘qwerty123’, ‘123456’ etc., should not be used even for testing purposes.
Eliminate the dangerous practice of hardcoding credentials
To meet various business needs, programmatic access to various IT resources and databases is required. Developers typically tend to hardcode the passwords on applications, scripts, and configuration files. Hardcoding should be avoided; instead, the passwords should be securely stored in a digital vault and the applications could programmatically access the credentials using APIs.
Check against compromised credentials
Periodically review the password usage across the organization and verify if any of the passwords used by employees match the list of compromised credentials available on the web.
Frequent password randomization
Passwords of corporate accounts should be randomized at periodic intervals – ideally once in 45 days or 90 days. It is reported that it takes a few months for hackers to exploit the stolen credentials. Periodic password randomization helps avoid credential abuse.
Strong access controls
Access to the passwords should be controlled strictly based on job roles and responsibilities. For sensitive assets, just-in-time access should be enforced.
Monitor critical metrics
Failed login attempts, number of password reset requests are some critical factors that should be continuously monitored. Abnormal patterns on these critical activities might be an indicator of an ongoing attack.
Password security is the foundation of information security. Internalizing this fact is critical to preventing a good number of attacks. Colonial pipeline attack should serve as a timely wake-up call. It is time to wake up to password security!
































![What is Cloud PAM? [Definition, Features, Benefits, and Factors to Choose the Right One]](/images/cloud-pam/cloud-pam-blog-image.webp)




























