One of the most difficult aspects of security in a Windows environment is keeping visibility to and control over Windows privileges. All too often, users are given more privileges than they actually need. This can lead to dangerous Windows Server privilege escalation that comes from an attacker gaining access to an account that has a high level of Windows Server privileges. In this post, we will look at Windows Server privilege escalation, why this is dangerous, and how your organization can effectively implement the tools and controls needed for effective least privilege management.
What is Windows Privilege Escalation?
Windows privilege escalation is a security risk where a standard user tries to gain elevated unauthorized access to privileged accounts. Attackers may use this to get around security measures, install malicious software, steal confidential information, or gain complete control of networks and systems.
Why should IT admins protect privileged accounts against privilege escalation?
Let's examine why privileged accounts are the target of privilege escalation attacks and why IT administrators need to safeguard them.
Privileged accounts are extremely sensitive accounts that need to be properly safeguarded, such as domain admin and service accounts. If hackers manage to get into these accounts, they will be able to gain unauthorized access to crucial accounts, which will result in a security risk. For instance, a leaked VPN or domain account credential from a former employee or a third party can be abused by cybercriminals to enter and establish foothold within an organization’s network. Security teams should place a high priority on protecting these accounts as privilege escalation attacks contribute to a vast majority of cyberattacks.
What are the dangers of Windows Server privilege escalation that IT administrators and enterprise security teams face?
Windows privilege escalation happens when an attacker is able to gain high levels of privileges on a target Windows host. It is a very valuable type of exploit used by attackers to compromise systems and facilitate other types of attacks. This usually happens in one of two ways:
- Overprovisioned accounts
- Exploiting an unpatched vulnerability
Overprovisioned accounts
A common issue with many applications is the level of privileges needed to run the application. Organizations may use a particular business-critical application that is poorly written from a security standpoint, leading to the requirement for local administrator privileges.
This leads to the user account getting granted administrator privileges on the machine simply to ensure there are no problems with running the application. Using native Windows Server tooling, it is challenging if not close to impossible to do away with admin privileges for user accounts required to run these types of applications.
Find out how EPM eliminates local admin rights with a personalized demo
Exploiting an unpatched vulnerability
Organizations need to also keep in mind the dangers of Windows privilege escalation that come from attackers capitalizing on vulnerabilities found on your Windows machines. This is another type of Windows privilege escalation that organizations must protect against primarily by keeping Windows hosts updated with the latest patches available.
What is the best way for organizations to handle windows least privilege management?
One of the best ways for organizations to protect their Windows environments is to enforce Windows Server least privilege across the environment. This means that end users have the least amount of privileges they need to carry out only those tasks they absolutely need to do.
As mentioned in the outset, having Windows users granted administrator privileges simply to run a particular application is a security risk that organizations need to give attention to. For the purposes of this discussion, this is the area we are going to key in on.
Businesses often face the security challenge of a business-critical application that needs to have administrator privileges on a Windows machine. This leads to granting administrator privileges to users who need to run the application. How can you go about enforcing least privilege to users while at the same time giving applications the privileges needed to run on a Windows host?
The important distinction that needs to be made with least privilege and application permissions is that it is the application that needs the permissions and not the user. However, the privilege and permissions model that is commonly employed today- involves assigning permissions to “users” and not applications.
How can you effectively provide the permissions to the applications in a way that allows controlling and restricting the administrator privileges needed to only the application and not to the whole system in general?
How does Securden Endpoint Privilege Manager support Windows least privilege management?
The challenge of least privilege and application administrator privileges is one that is easily solved by Securden Endpoint Privilege Manager (EPM). With Endpoint Privilege Manager, administrators can configure specific applications that are allowed for administrator escalation and then assign the privileges for that application to specific users who are allowed to launch the application with the privileges needed.
With this approach, administrator privileges are not given to the entire user session by way of making the user a member of the local administrators group on the local Windows host. Rather, the administrator privileges are granularly applied to the specific application for a specific user.
Get started with a free EPM trial and gain visibility in your organization.
How can IT admins grant administrator privileges for specific applications without jeopardizing security?
Let’s take a look at a scenario where IT admins apply administrator privileges to a specific application for a specific user and see how this can be done using the tools that Securden Endpoint Privilege Manager provides.
Suppose a user has a need to start/stop services in services.msc OR use inetMgr.exe as an example. Traditionally, the user may simply be placed inside the local administrators group on the local Windows machine. This would allow them to run the applications as administrator, however, would allow the user to have carte blanche admin privileges on the system.
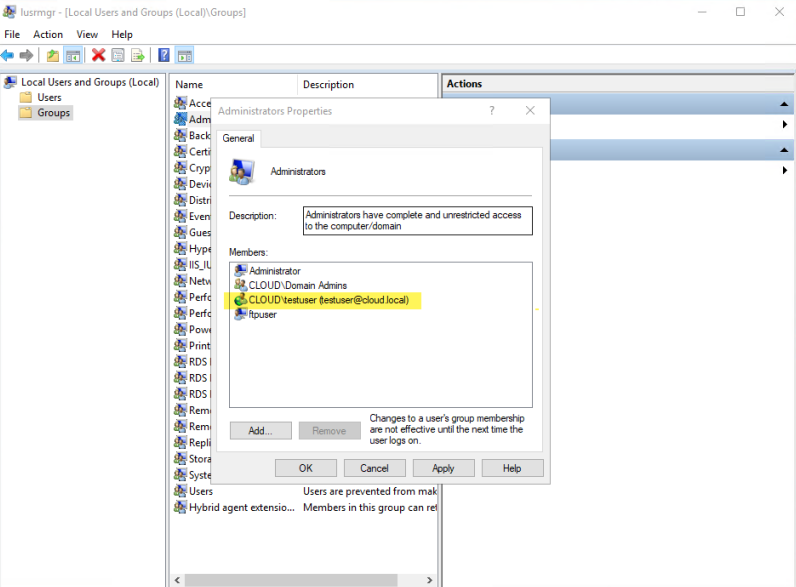
Traditionally users have to be added to administrators group to run apps with administrator privileges
The better way is to use an application policy that allows assigning the admin permissions on an application-by-application basis. Let’s add the services.msc and inetMgr.exe application to Securden WPM and assign a policy to the underprivileged user to allow running these applications as an administrator.
Securden WPM provides detailed granularity in how the application policy is applied. We can assign a particular application to be allowed for a specific computer and for a specific user.
Now, logged in as an underprivileged user, the user can run services.msc or inetMgr.exe as an administrator using Securden WPM. You may note that even though we logged in as an underprivileged user, the application is run as an administrator.
Concluding Thoughts
Windows privilege escalation is an attack that organizations must give due time and attention. In addition to keeping Windows systems patched, enforcing least privilege access across the board is a great way to minimize the risk of compromised accounts with overprovisioned privileges.
With Securden Endpoint Privilege Manager, organizations have the ability to drastically reduce the attack surface that comes from giving end users local administrator privileges on Windows hosts simply to run certain applications. Applications can be granularly defined to run as an administrator for a specific user, on specific Windows computers.
Windows Privilege Escalation FAQs
1) How do IT admins prevent privilege escalation on the systems within the organization?
IT admins can prevent the systems in their organization from privilege escalation by
- Removing excess access rights and granting minimum privileges
- Updating the system regularly
- Implementing robust password management solution
- Auditing user activities
2) Should admin rights ever be granted to end users?
No. End users should not be granted admin rights. Instead, they should be provided with the least privileges needed to carry out the tasks based on their role. If a user needs administrator rights for an urgent task, they should raise a privileged access request.
3) What are vertical vs. horizontal escalations?
Vertical escalation is nothing but a normal user with the least privileged rights gaining excess access rights more than necessary. Whereas horizontal escalation is gaining access to another user’s account without elevating admin privileges.
4) What are some of the most common privileged accounts that attackers go after?
The most common privileged accounts attackers target is:
- Domain Admin Account
- Privileged Account
- Local Admin Account
- Service Account
- Emergency Account
- Application Account
- Domain Service Account
5) What are some common techniques used for Windows Privilege Escalation?
Some common techniques used for Windows Privilege Escalation are listed below:
- Exploiting unpatched local vulnerabilities.
- Violating insufficient service permissions.
- Token impersonation.
- DLL hijacking.
- Bypassing User Account Control.
- Misconfigured scheduled tasks.
































![What is Cloud PAM? [Definition, Features, Benefits, and Factors to Choose the Right One]](/images/cloud-pam/cloud-pam-blog-image.webp)




























