This article discusses how admin rights are used in the organization, how they could potentially be misused, and how to mitigate the risks associated with local admin rights without dragging down employee productivity.
Where and why are admin rights used in organizations?
Admin rights are often granted to employees because they guarantee that the employees do not face permission-related hurdles in fulfilling their job responsibilities and completing their tasks. Granting local admin rights to end users is highly risky as admin rights grant complete control over their endpoint. The possibilities are endless. They could unknowingly click a malicious email attachment and end up crippling the entire IT network.
Why do IT admins insist on removing local admin rights?
Apart from the standard IT security concerns, IT administrators working across different industries face a common challenge. They must demonstrate compliance with regulatory requirements such as GDPR, SOX, NIST, NERC-CIP, PCI-DSS, ACSC Essential Eight, UK’s Cyber-essentials, and HIPAA. All these regulations advise organizations to grant the minimum level of permissions required to users across the organization. Local admin rights grant users much more permission on their endpoint than they absolutely need.
Therefore, IT admins claim that the first step for adhering to this requirement is to remove admin rights.
Is removing admin rights the right way to address privilege misuse?
Imagine a situation where a standard user (void of admin rights) needs to run applications with admin rights to complete their task. They must raise a ticket with their IT helpdesk team and sit tight while the helpdesk processes the request and work their way through protocols and eventually grant the required permissions.
While the process exists to keep the organization secure from threats, the security it offers comes at a steep cost to business productivity. As a principle, security should never come at the expense of employee productivity or business efficiency. The recommended way of going about local admin rights management is to remove admin rights and grant standard users the minimum level of privileges and permissions required to accomplish their tasks.
In other words, organizations must remove admin rights and enforce the principle of least privilege.
The following steps must be taken when removing admin rights and enforcing the principle of least privilege.
- Identify where admin rights exist
- Implement workflows to accomplish the task as a standard user
- Remove admin rights and demote local administrators to standard users
How to identify local admin accounts on endpoints?
Local admin accounts that exist in an endpoint can be enumerated using many methods. These methods may vary for different operating systems.
How to identify local admin accounts on Microsoft Windows devices?
On Windows, anyone can see the list of active users from the computer's login screen.
Alternatively, the list of user accounts on a device can be listed using the command “net users” in the command prompt.
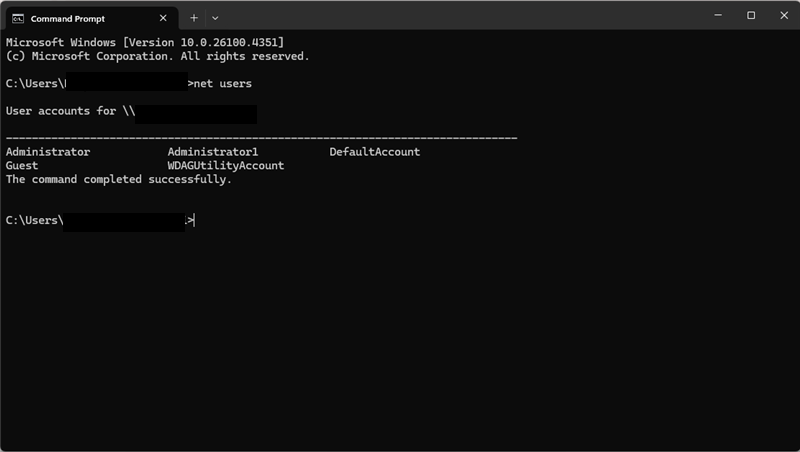
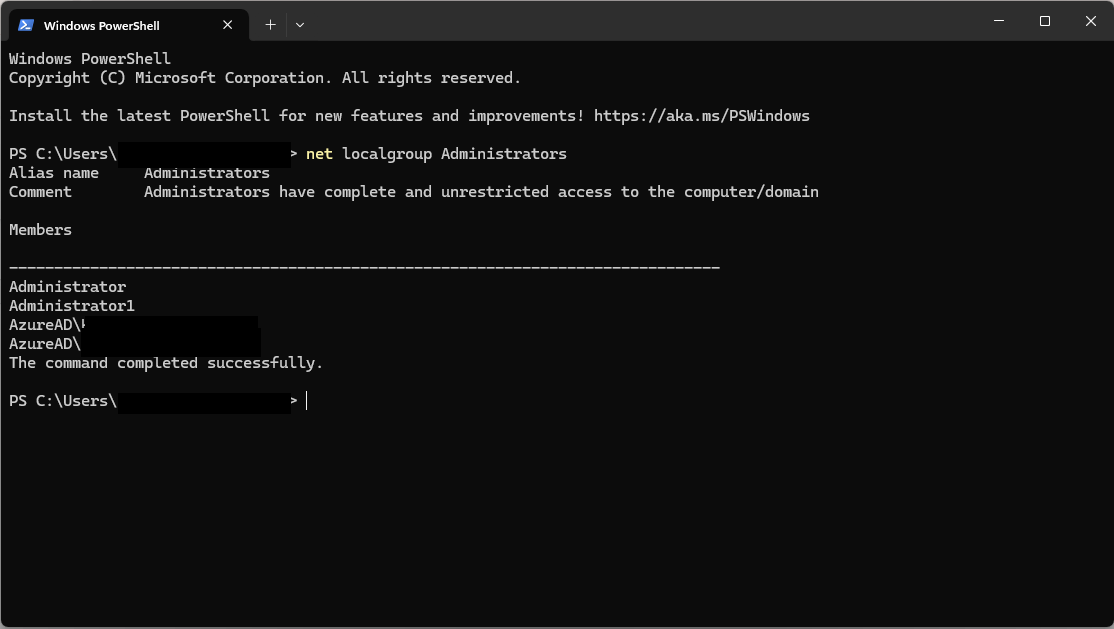
To view the members of the local administrator group, you may make use of the “net localgroup Administrators” command in the command prompt. The parent command “net localgroup” displays the list of all local user groups on an endpoint.
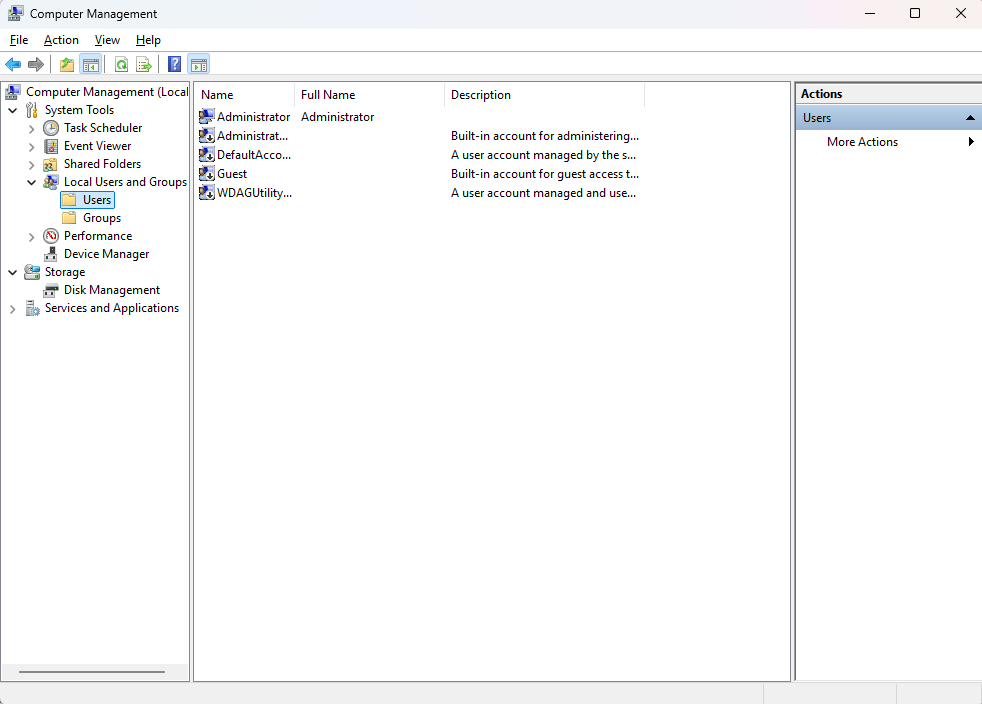
The list of users and groups can also be viewed outside the command prompt. You can make use of the computer management console to view the list in a GUI. The computer management console can be launched from the run command using “compmgmt.msc”.

In the computer management console, you can view the list of users and local groups by navigating through the directories in the LHS.

The list of user accounts can be viewed from the Control Panel >> User Accounts >> View Other Accounts. Here, all accounts that are not explicitly disabled or hidden are displayed.
How to list down the admin accounts on Mac Devices?
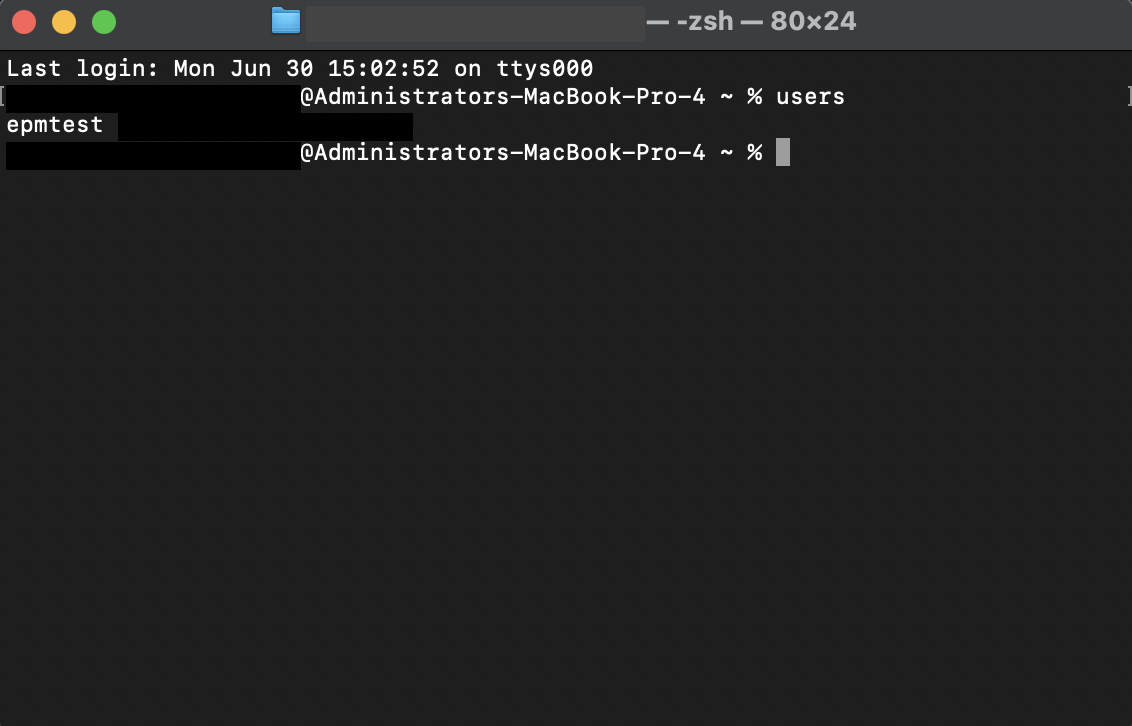
To view all the local user accounts that are present in a Mac device, running a simple command using the terminal would suffice. Open terminal and run the following command.
users
You will get an output similar to the image below.
Alternatively, the list of users on a Mac device can be viewed from the Settings app. Search for Users & Groups in Settings and the list of users will be displayed.
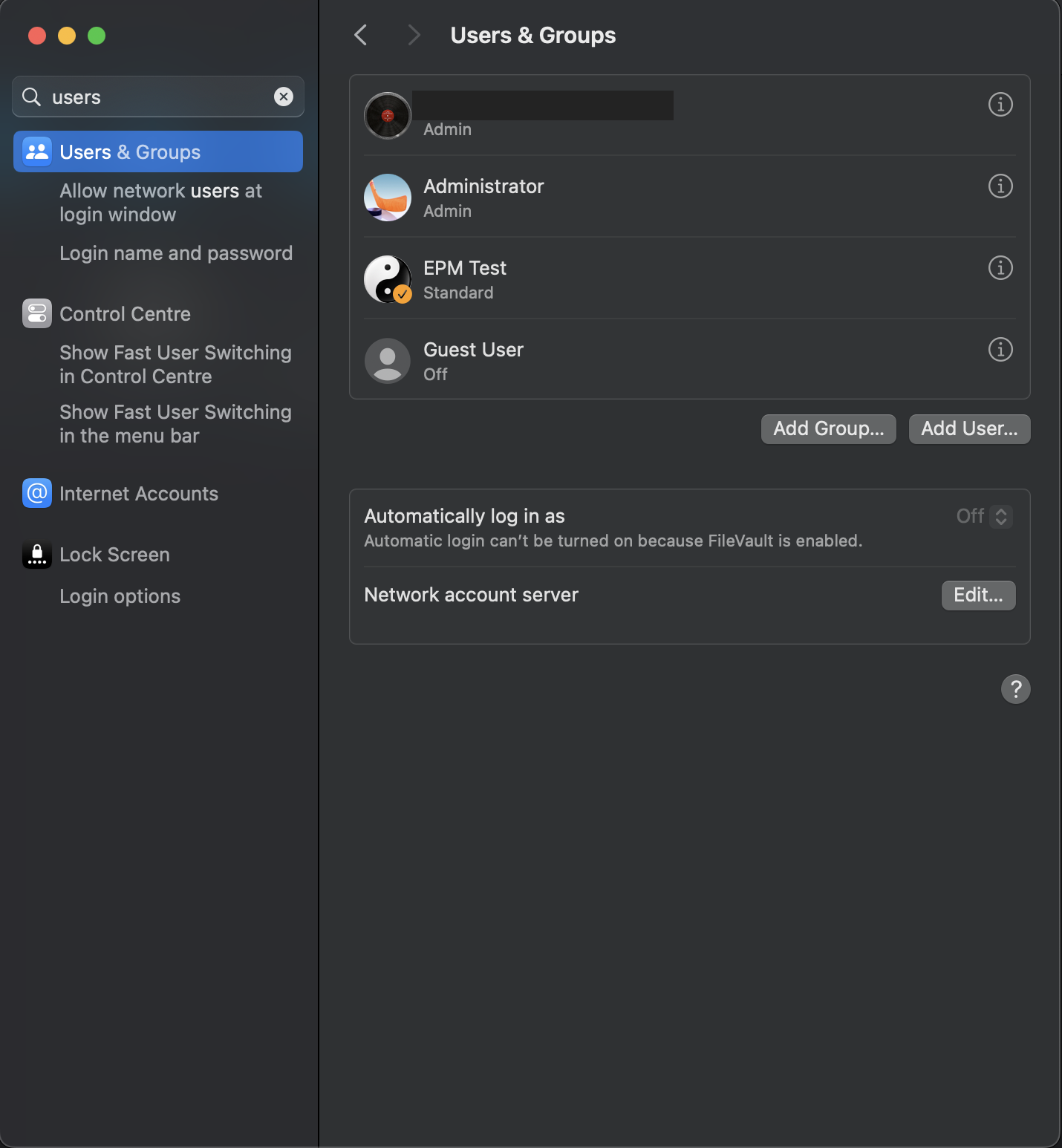
How to list the admin accounts on Linux Devices?
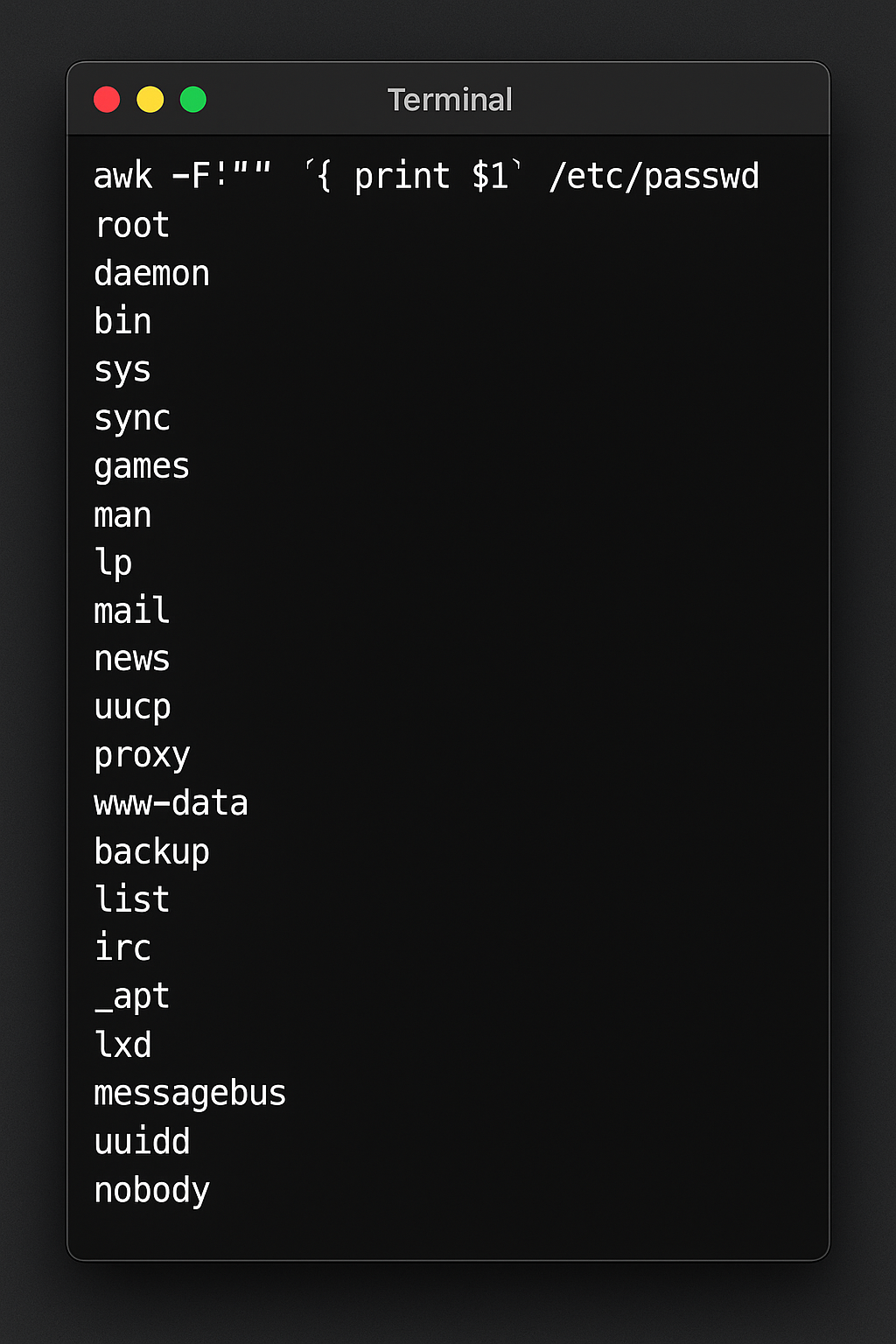
To view the usernames of all users in a Linux device, users can make use of the awk command. In the terminal, use the following command to display the list of usernames of all users available in the Linux device.
awk -F':' '{ print $1}' /etc/passwd
Sample output:
To check which users are a part of the root group, use the command below:
grep root /etc/group
All the methods discussed above are available to see the list of users, root users, and administrators on devices running Windows, Mac, and Linux, they work only on individual machines. How would a large enterprise know which accounts have admin rights in their network of a thousand endpoints? We will discuss below.
How to list all the local admin accounts in a network of devices?
To have central oversight over admin accounts across multiple devices in an organization, you can make use of the local admin analysis capabilities of Securden Endpoint Privilege Manager.
Once the agent is deployed on all the endpoints,
The agent fetches all the local user accounts and lists them down in the central server for the IT admin.
The IT administrator will be able to see all the user accounts that exist on each endpoint just by selecting the required computer.
Fetch the list of applications that require admin rights to run from all the computers.
Once we find out the list of admin rights on endpoints, we need to find a way to eliminate admin rights with minimal impact on the workforce's routines and their productivity. We will discuss this in the next section.
How to remove admin rights with minimal impact on the workforce?
Removing admin rights can be quite a disrupting move. Many users need admin rights to run certain applications or perform administrative changes as part of their responsibilities. We can remove the admin rights and cause no loss in employee productivity by elevating specific applications when required in the least invasive manner possible.
For example, if a database administrator needs admin rights to run MSSQL server, and a database backup application from time to time, the database administrator must be able to do so without any external intervention.
This is possible through policies designed to suit specific users and their permission requirements. To design such policies, we need to know
Which users are using admin rights?
What applications are these users running with admin rights?
Which users are installing applications often?
To know such details accurately in large enterprises with multiple functional teams is a monumental task. You can make use of the Securden Agent to get these insights. We will discuss how to use the agent for this purpose in the next section.
Analyzing the Use of Admin Rights on Endpoints
Apart from fetching the list of local users from endpoints, the agent fetches the applications and commands that are run with admin/root privileges on endpoints across the organization. Once fetched, the apps and commands are then added to the central repository. The agent also tracks which applications are frequently run with admin rights and provides insights to the IT administrator through reports.
With these insights, the IT administrators can make informed decisions while devising workarounds for standard users to help them get their job done with minimum privileges and permissions.
Removing Admin Rights and Enforcing the Principle of Least Privilege
Once the list of local users and their application usage data are available, the IT administrator can create policies that can elevate specific applications for specific users on their designated devices.
It is advisable to create these policies before removing admin rights as this step ensures the productivity of the workforce doesn’t take a nosedive right after the local admins are demoted to standard users.
Once the policies are in effect, the IT admin can safely remove admin rights directly from Securden. The Endpoint Privilege Manager interface has provisions to directly remove the admin rights of users and move them from one AD user group to another.
Policy based privilege elevation
Once the admin rights are removed, the policies that are enforced will take care of elevating apps that are regularly used by the users.
On-demand privilege elevation
In scenarios where users need to elevate apps that are not covered by existing policies, users will be able to raise a request with the IT admin. The IT admin can evaluate the merits of the request and grant time limited elevated access to the application. Here the IT admin can optionally create a new policy for the requested app.
Time-limited, temporary local admin rights
In rare cases where users such as technicians or developers need to elevate multiple apps at the same time to fulfill their responsibilities, they can avail themselves of time-limited, temporary full admin access after going through a request-release workflow.
By removing unnecessary privileges from users and granting them just the minimum level of permissions and privileges to help them complete their tasks, Securden Endpoint Privilege Manager helps prevent privilege misuse, and enforce the principle of least privilege successfully.
Book a personalized demo with our experts today!
































![What is Cloud PAM? [Definition, Features, Benefits, and Factors to Choose the Right One]](/images/cloud-pam/cloud-pam-blog-image.webp)




























