Last week, I came across an interesting research on cybersecurity practices during the past decade (2010-20) by Jean-Christophe Gaillard, a UK-based cybersecurity strategist. Jean candidly explains how even large firms which have had fully functioning information security teams have ignored the cybersecurity basics and are struggling with various issues now.
Jean’s findings and comments set me thinking.
During the past two decades (or close to that), I have had the opportunity to interact with IT professionals on varied topics across the globe in person and through various media, forums, and online communities.
While many cybersecurity practices have changed or evolved over the years, one particular practice strikingly remains the same - then and now: the way organizations and IT teams handle sensitive passwords. It has been two decades, but the story remains the same!
Any firm dealing with IT, obviously deals with passwords and other types of credentials too. Unless forced by industry regulations or until facing a security incident themselves or hearing about a compromise in a similar business, firms do not attach much importance to password security.
Certain practices hardly change!
Attackers royally walk-in
As the popular saying goes, hackers nowadays don’t actually hack into networks; they simply royally walk-in using stolen, weak, or compromised credentials freely available on the dark web.
TechTarget provides a wonderful definition for the phrase ‘data breach’: “... an incident in which sensitive, protected, or confidential data has potentially been viewed, stolen, or used by an individual unauthorized to do so..”
At the root of many data breaches lies the involvement of stolen credentials or misuse of administrative access. Yet, the all-important password security measures remain one of the most neglected basic security measures.
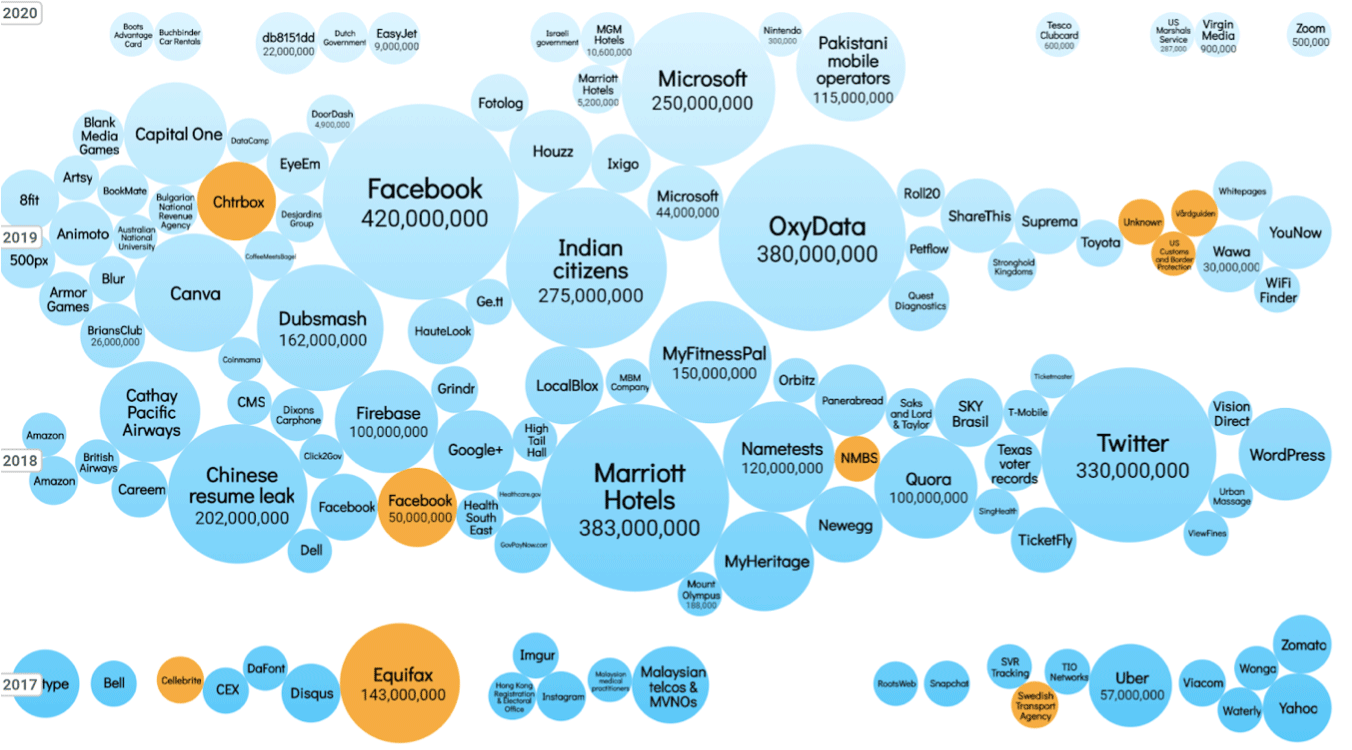
Source:Information Is Beautiful
Time and again security researchers and industry analysts stress that more than 80% of the data/security breaches worldwide involve stolen credentials or misuse of administrative access.
Losing sight of the security basics
Many organizations are struggling to enforce password policies. While IT Managers understand the importance of using strong, unique passwords that help combat identity-based attacks, it is common to see the same passwords assigned to multiple IT assets; developers reusing passwords across their personal and work accounts; passwords on spreadsheets circulated across departments; a departing IT staff exiting with a copy of all the credentials, and similar practices.
When developers reuse passwords, a compromise of one of their personal accounts gives hackers easy access to corporate data. Uncontrolled or unmonitored access often leads to exploitation by malicious insiders. Weak security practices and vulnerabilities in the supply chain lead to breaches upstream.
During the recent years, lack of basic security measures and failure to adopt the best practices in password management, IT access controls, MFA enforcement, and patch management have led to some of the worst data breaches. While concentrating on deploying sophisticated and advanced security technologies, these companies lost sight of the basics leading to financial and reputation loss.
Password Management - the foundation of information security
Data breaches and security incidents happen due to a variety of reasons. Not all security incidents can be prevented - there is no magic wand or a silver bullet available yet. But it has been proved time and again that identity thefts remain at the root of a majority of the data breaches and cyberattacks.
By concentrating on the basic password security best practices, IT departments can indeed prevent a good number of attacks. Strong, unique passwords are still effective when periodically randomized. Password management is indeed the foundation of IT security.
Password management is not just about ensuring strong, unique passwords. It extends to entire lifecycle management, monitoring, and controlling access. You can establish a centralized vault, granularly control ‘who’ can access ‘what’; automate password security best practices; rotate passwords of IT assets at periodic intervals; grant RDP, SSH, SQL connections with IT assets without revealing passwords; maintain a complete record of all activities, and gain visibility over all IT access.
Identity Theft Protection Services
Identity theft protection services that offer monitoring and recovery services for your personal information could be of help. These services scan the web for signs of unauthorized activity and help you recover your identity. Regardless of how much or how little you use the internet, you may be at risk for identity theft. A good identity theft service actively monitors all your accounts and personal information and alerts you as soon as it encounters any unusual activity. For example:
- Phishing - A suspicious email that sends you down a rabbit hole of links. These links then redirect you to web forms that request that you enter personally identifiable information. Once it’s completed, they have you.
- Formjacking - This is when fraudsters insert malicious code into the billing section of legitimate websites when you make an online purchase. The code scans and steals your billing information.
When there’s a security breach, time is of the essence. It can mean the difference between a few minutes to secure your accounts, or lasting personal and financial damages.
Decades-old practices should change
Though the death of passwords is being predicted for so long, passwords still remain the first authentication measure for most types of IT access. Despite the emergence of passwordless authentication technologies, passwords/identities remain the top choice.
The password is still the undisputed king of authentication. Passwords are here to stay and password security is one of the foundational measures. The sooner organizations ditch the decades-old spreadsheet approach and adopt advanced password management, the better equipped will they be to combat data breaches.

































![What is Cloud PAM? [Definition, Features, Benefits, and Factors to Choose the Right One]](/images/cloud-pam/cloud-pam-blog-image.webp)




























