How to Create Application Control Policies for Windows Devices?¶
Windows application control policies govern application privileges and permissions for users on Windows devices.
The EPM administrator can create application control policies for specific applications and application groups. When creating, the admin can associate the policy with specific computers and users to granularly control application usage and privileges.
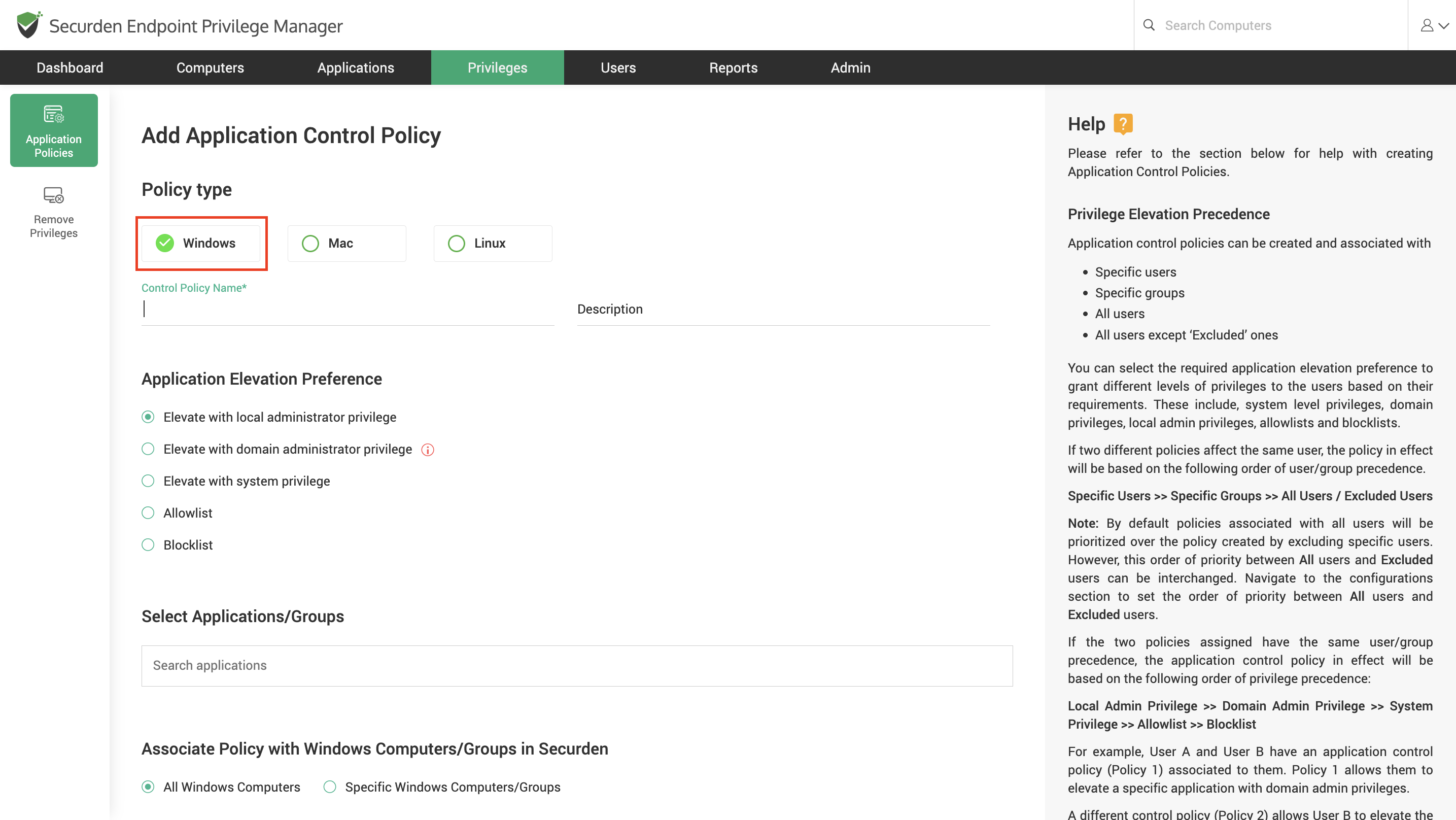
To create a Windows policy, navigate to Privileges >> Add Policy, select Windows Policy as the policy type and follow the steps below.
-
Provide a name and description for the policy.
-
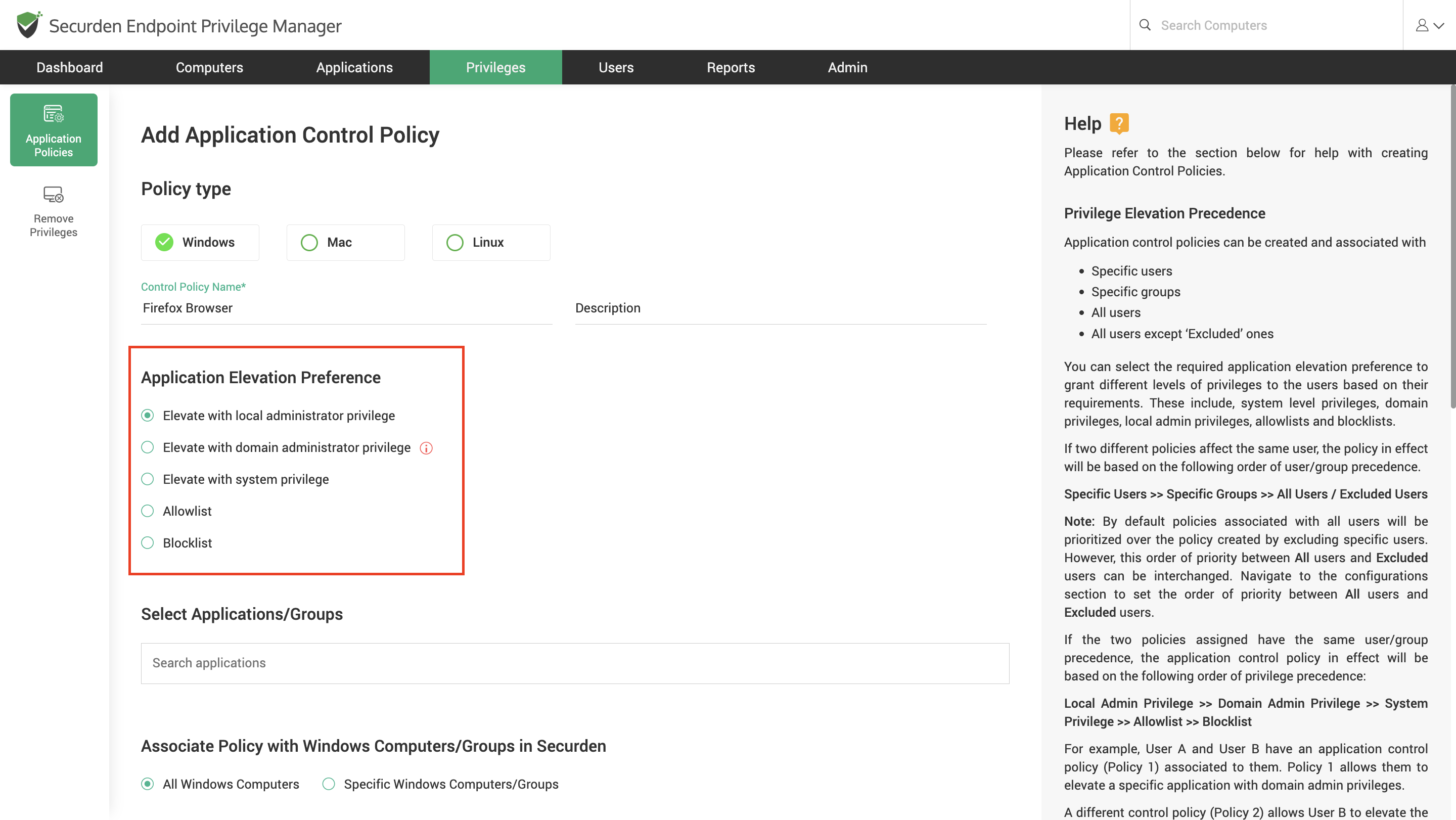
Select the application elevation preferences. Here, you can choose to create an application control policy, or a privilege elevation policy.
Application Control Policies govern which application a user can run. They are of two types, allowlists and blocklists.
-
Allowlists – An allowlist allows the associated user to run the specific apps with the default permissions of the user account. All other apps are blocked for the user.
-
Blocklists - A blocklist blocks the associated user from running specific apps completely. The user is free to run all other apps.
Privilege Elevation Policies are used to grant higher access to specific applications and application groups. When enforced, these policies allow the user to run the application with admin privileges. You can select the elevation preference when creating a privilege elevation policy. You can choose between elevating with local administrator, domain administrator, and system privileges.
-
Elevate with local administrator privilege – When this right is granted, the user will be granted permission to run the associated applications with local admin privileges.
-
Elevate with domain administrator privileges - When this right is granted, the user will be granted permission to run the associated applications with domain admin privileges. This can be disabled from Admin >> Configurations.
-
Elevate with system privilege – When this right is granted, the apps/processes will run with system privileges.
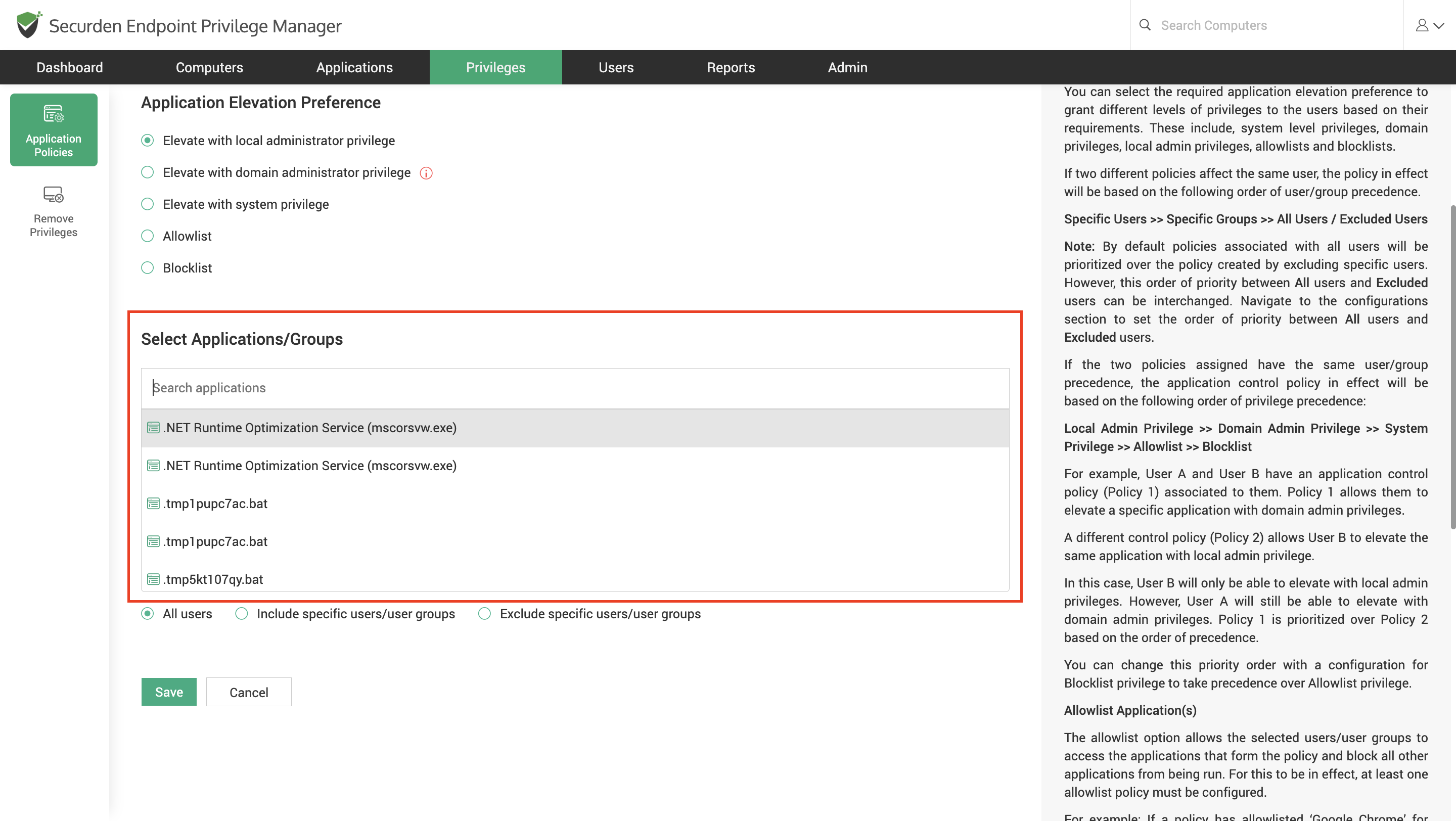
Once the preferences are set, you can proceed to associate the policy with applications, users, and devices.
-
-
Select the applications that must be added to this control policy.
-
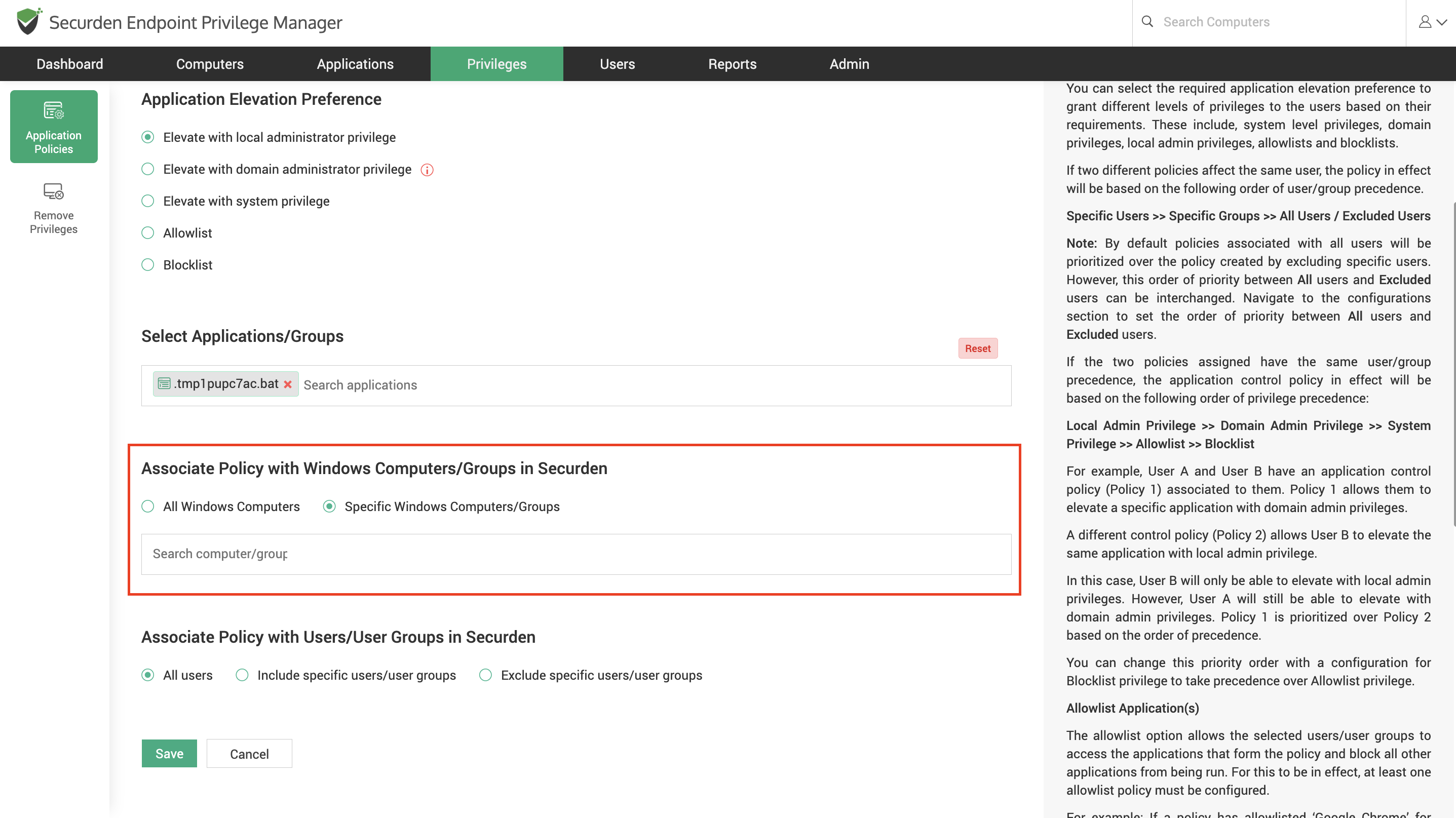
Select the computers/computer groups this policy should apply to. You can do this through different methods. You can associate specific computers or associate the policy with every device in Securden.
- Typically, policies that block malicious applications are associated with all devices to provide organization-wide protection. Policies that grant elevated access to specific applications should always be associated only with the required devices.
-
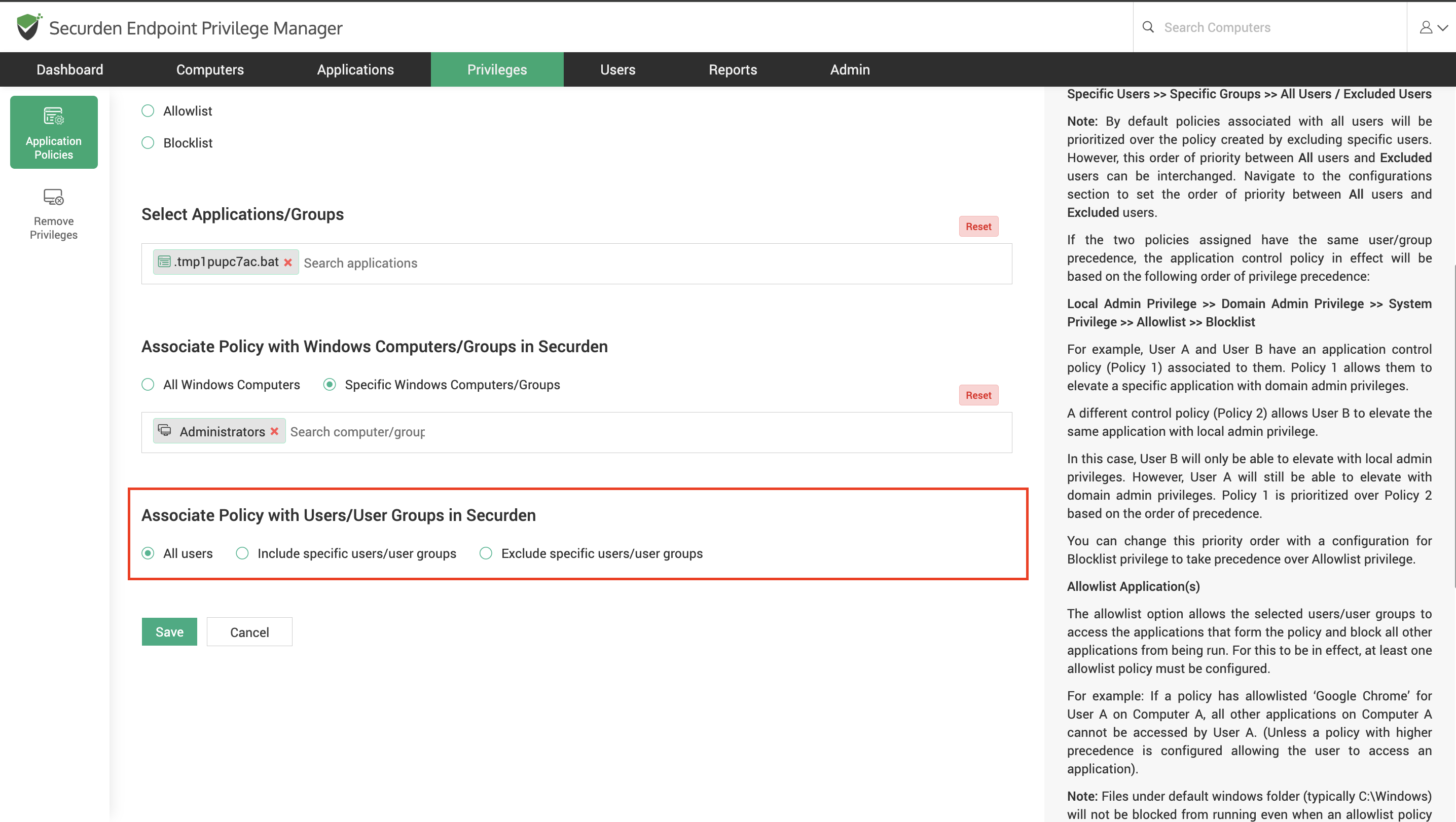
Select the users/user groups for whom the policy is intended. You can include specific users or exclude certain users and associate the policy with every other user in the EPM.
-
Once the preferences are selected, Save the policy.
When a policy is associated with a specific domain device and a specific domain user, the user can only exercise this policy on the specific device. All conditions must be satisfied in order for the policy to kick in.
Note
When two or more policies affect a user on a device, the policy in effect would follow the order of precedence as follows.
Specific Users >> Specific Groups >> All Users / Excluded Users
For example, if two policies A and B exist and A is associated with a specific user (say Alex) and B is associated with all users, then for Alex, policy A will apply.
If the two policies are at the same precedence level (based on users and user groups), then the following criteria (based on privilege elevation preferences) would be used to select the policy to be enforced.
Local Admin Privilege >> Domain Admin Privilege >> System Privilege >> Allowlist >> Blocklist
For example, if two policies A and B exist and both are associated with the two different groups. Let’s say Alex is a user who is part of both groups. If policy A grants Local Admin Privilege and policy B is a blocklist policy, then policy A will be enforced for Alex.