How to self-support remote password reset for any SSH-enabled device
You can define customized templates to carry out remote password resets on devices that can be connected through Secure shell (SSH) such as Linux devices, routers, server hardware, etc. You can define a command or a sequence of commands to be used for carrying out the password reset activity in the form of a template.
Typically, the same template can be used for multiple devices that follow the same commands. So, after defining the templates, you can associate them with the required account types in PAM.
How to Create SSH Templates in PAM
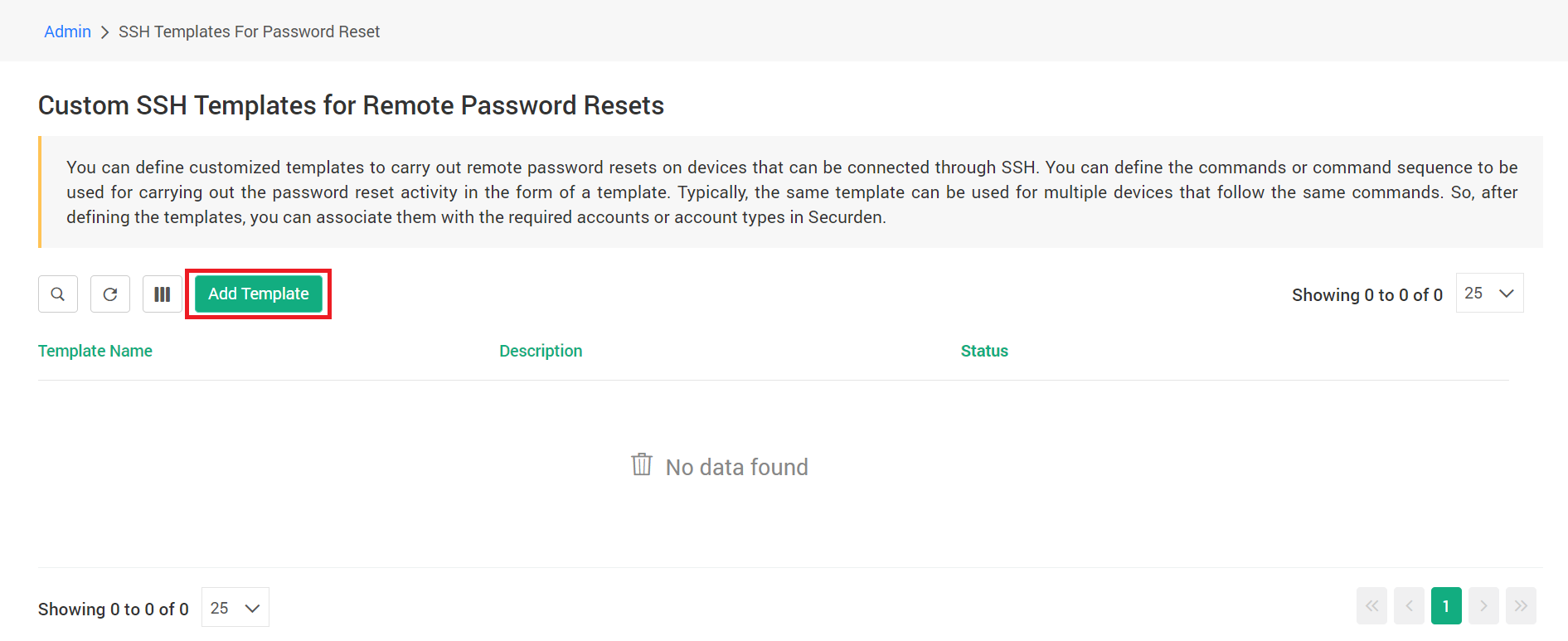
To create an SSH template, navigate to Admin >> Account Management >> SSH Templates for Password Reset in the GUI.
Step 1: Create a template
Click on ‘Add Template’. In the GUI that opens, you need to specify the attributes for the template creation. You will have two options - one to enable remote password verification and another to create a command sequence for password reset.
Step 2: Define the template name and description
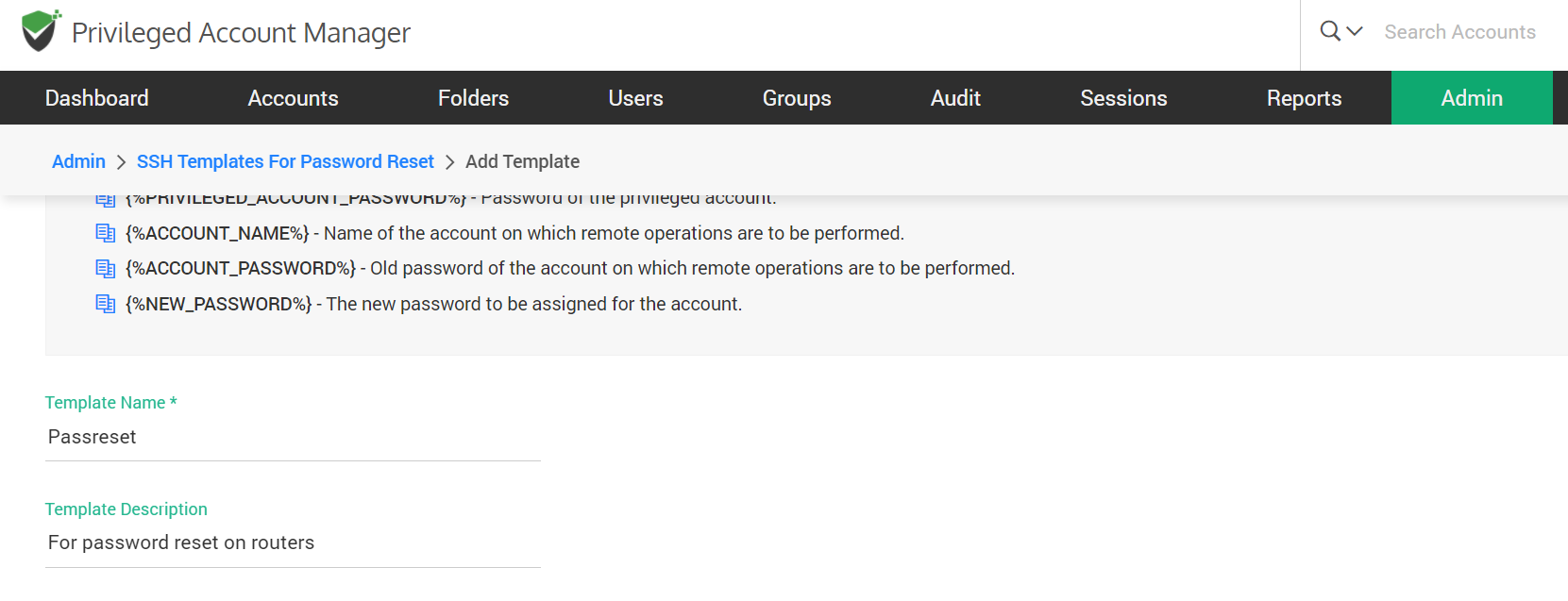
- Add a template name: The name that you enter here helps you uniquely identify the template being created. This name will appear on the SSH template list in Securden.
- Add a template description: This explains an overview of the template and the purpose behind the creation of the template
Templates can be created for two types of activities - (1) for verifying if the password stored in Securden is in synchronization with the actual password on the resource, and (2) for carrying out a remote password reset. You can choose either or both.
Step 3: If you are creating the template for password verification
You have the option to verify the password if it is in sync with the password for the account on the remote device. This can be done either via remote login or you can define a command sequence to be run which will check for verification.
You can verify if the password stored in Securden is in synchronization with the actual password on the remote resource. This can be done either by trying to remotely log into the device or by defining a command sequence to be executed. Select an option that works best for you.
When ‘Enable remote password verification’ is chosen:
- To enable verification via remote login, simply click ‘Remote login’. Securden logs into that account in the remote machine to check if the password is in sync.
- When ‘Command Sequence’ for password verification is chosen, you will be required to insert a command.
Inserting a command
A sequence of commands is given to the remote machine to perform password verification. You can use the placeholders for replacing the attributes in the respective commands:
Example:
sudo passwd {%ACCOUNT_NAME%} {%PRIVILEGED_ACCOUNT_PASSWORD%} {%NEW_PASSWORD%} {%NEW_PASSWORD%}
Placeholders for Attributes :
{%REMOTE_LOGIN_ACCOUNT_NAME%} - Name of the account for remotely logging in to the IT asset.
{%REMOTE_LOGIN_ACCOUNT_PASSWORD%} - Password of the remote login account.
{%PRIVILEGED_ACCOUNT_NAME%} - Name of the account that has privileges to do remote operations.
{%PRIVILEGED_ACCOUNT_PASSWORD%} - Password of the privileged account.
{%ACCOUNT_NAME%} - Name of the account on which remote operations are to be performed.
{%ACCOUNT_PASSWORD%} - Old password of the account on which remote operations are to be performed.
{%NEW_PASSWORD%} - The new password to be assigned for the account.
- The ‘Description’ of the command is optional and can be given for recognizing its use.
- The ‘Timeout’ is the number of seconds the system will wait to get required resources for executing a command. Once the timeout is reached, the command returns as unexecuted resulting in an unsuccessful attempt made for password verification.
- Error Handling: To assess if the execution of a command has resulted in any errors you need to define all the possible errors in this field. You may enter multiple error messages separating each entry into different lines. When Securden encounters any of the entered errors, the process execution stops, and password verification will not happen. This also serves as a useful Syslog detail for SIEM solutions in case your organization uses one.
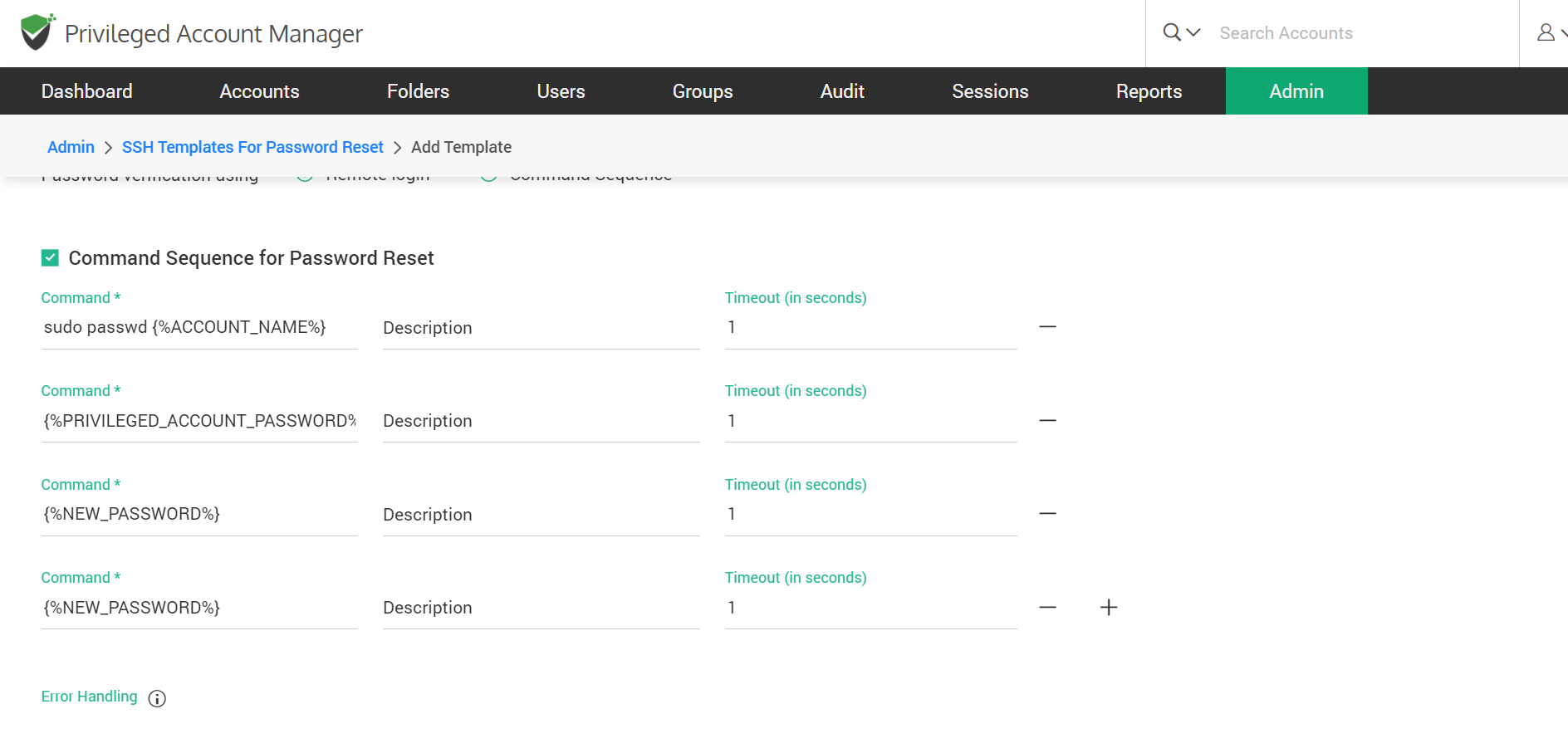
If you are creating the template for remote password reset
You can configure remote password reset for any SSH-enabled device. Typically, you will be defining the required command or a sequence of commands to be run to carry out password reset in the template. You can make use of certain placeholders in the command and Securden will fill the values at runtime.
To configure a template for remote password reset,
- Click ‘Command sequence for password reset’
- Insert a command sequence
Example of a command sequence to reset password:
sudo passwd {%ACCOUNT_NAME%} {%PRIVILEGED_ACCOUNT_PASSWORD%}
{%ACCOUNT_PASSWORD%} {%NEW_PASSWORD%}
You may use the following placeholders for replacing the attributes in the respective commands:
- {%REMOTE_LOGIN_ACCOUNT_NAME%} - Name of the account for remotely logging in to the IT asset.
- {%REMOTE_LOGIN_ACCOUNT_PASSWORD%} - Password of the remote login account.
- {%PRIVILEGED_ACCOUNT_NAME%} - Name of the account that has privileges to do remote operations.
- {%PRIVILEGED_ACCOUNT_PASSWORD%} - Password of the privileged account.
- {%ACCOUNT_NAME%} - Name of the account on which remote operations are to be performed.
- {%ACCOUNT_PASSWORD%} - Old password of the account on which remote operations are to be performed.
- {%NEW_PASSWORD%} - The new password to be assigned for the account.

- The ‘Command’ holds the placeholder and the command to be run for resetting the password for the attribute selected using the placeholder.
- The ‘Description’ of the command is optional and can be given for recognizing the use of the command or a short brief of what it does.
- The ‘Timeout’ is the time in seconds that the command waits until moving to the next command in the sequence. This is done in case there are delays in running the preceding command.
- Error Handling: To assess if the execution of a command has resulted in any errors you need to define the possible errors in this field, You may enter multiple error messages separating each entry in different lines. When Securden encounters any of the entered errors, the process execution stops, and password reset will not happen. This also serves as a useful Syslog detail for SIEM solutions in case your organization uses one. The password change success and failures are Audited in Securden.
Save changes
Important Note: For security reasons, the template created by one administrator will have to be approved by another administrator before it can be put to use.
How to Manage SSH Templates in PAM
The templates created in Securden can be edited or deleted anytime from the GUI. This can be done by clicking the “Actions” icon. You can perform the following actions:
- Edit template name and description
- View status: Shows if an added template has received approval, waiting to be approved, active or inactive.
- View template: Gives an overview of the template and the attributes enabled for it.
- Edit template: This lets you redefine the template attributes and fields.
- Delete template: On clicking the delete button, a secondary confirmation popup will appear, on clicking ‘Ok’ it will be deleted from Securden.
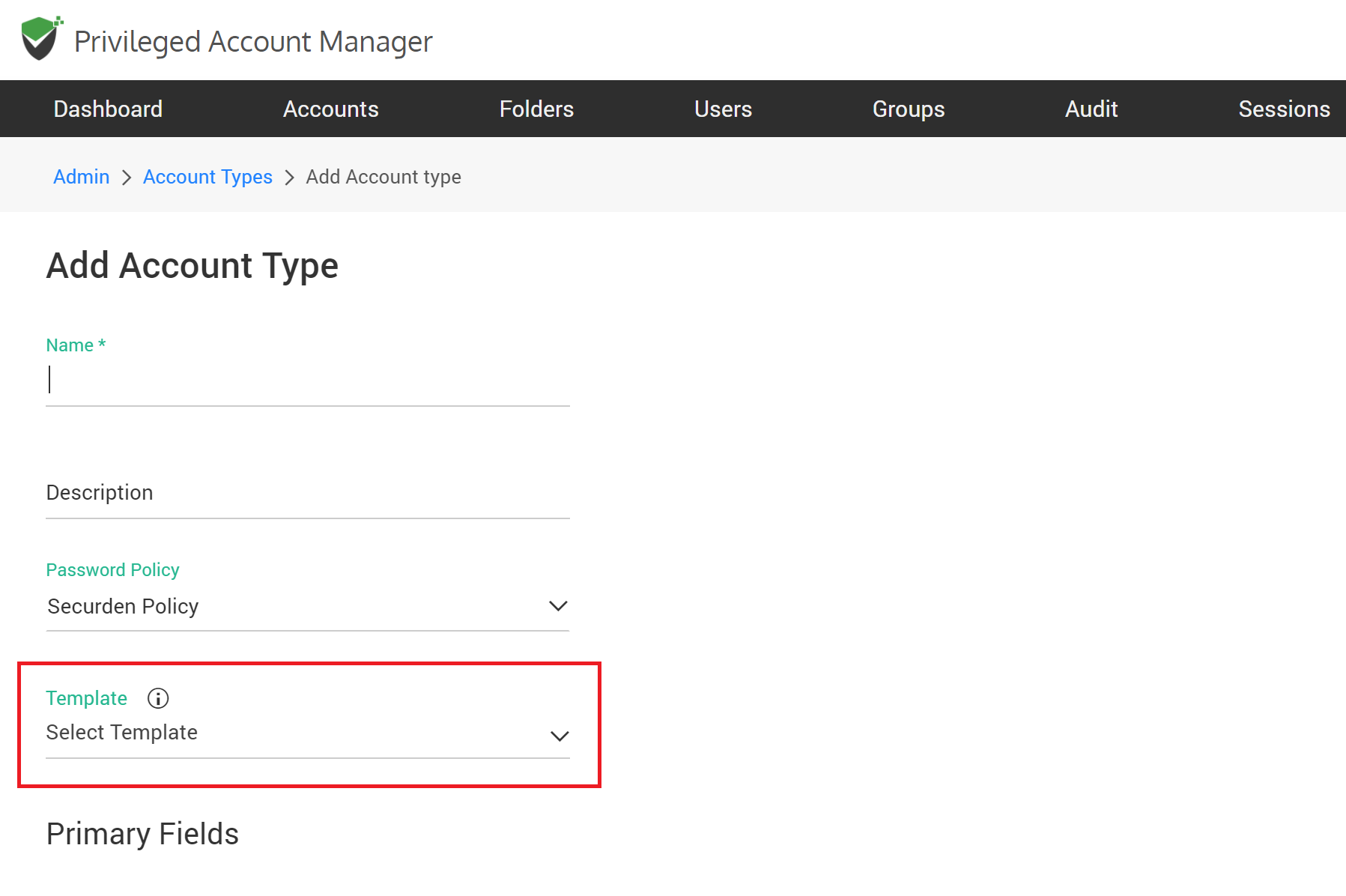
How to Associate SSH Templates with an Account Type
The templates that are duly approved by another administrator, can be associated with the required account types. Once you associate, the accounts belonging to that specific type will get remote password reset and/or password synchronization verification capabilities.
Templates can be associated when creating a new account type. They can’t be associated with existing account types.
To associate a template, you need to create a new account type. To do that, navigate to Admin >> Account Management >> Account Types and click the ‘Add’. In the GUI that opens, you will see a drop-down named ‘Template’. You may select the template to be associated.