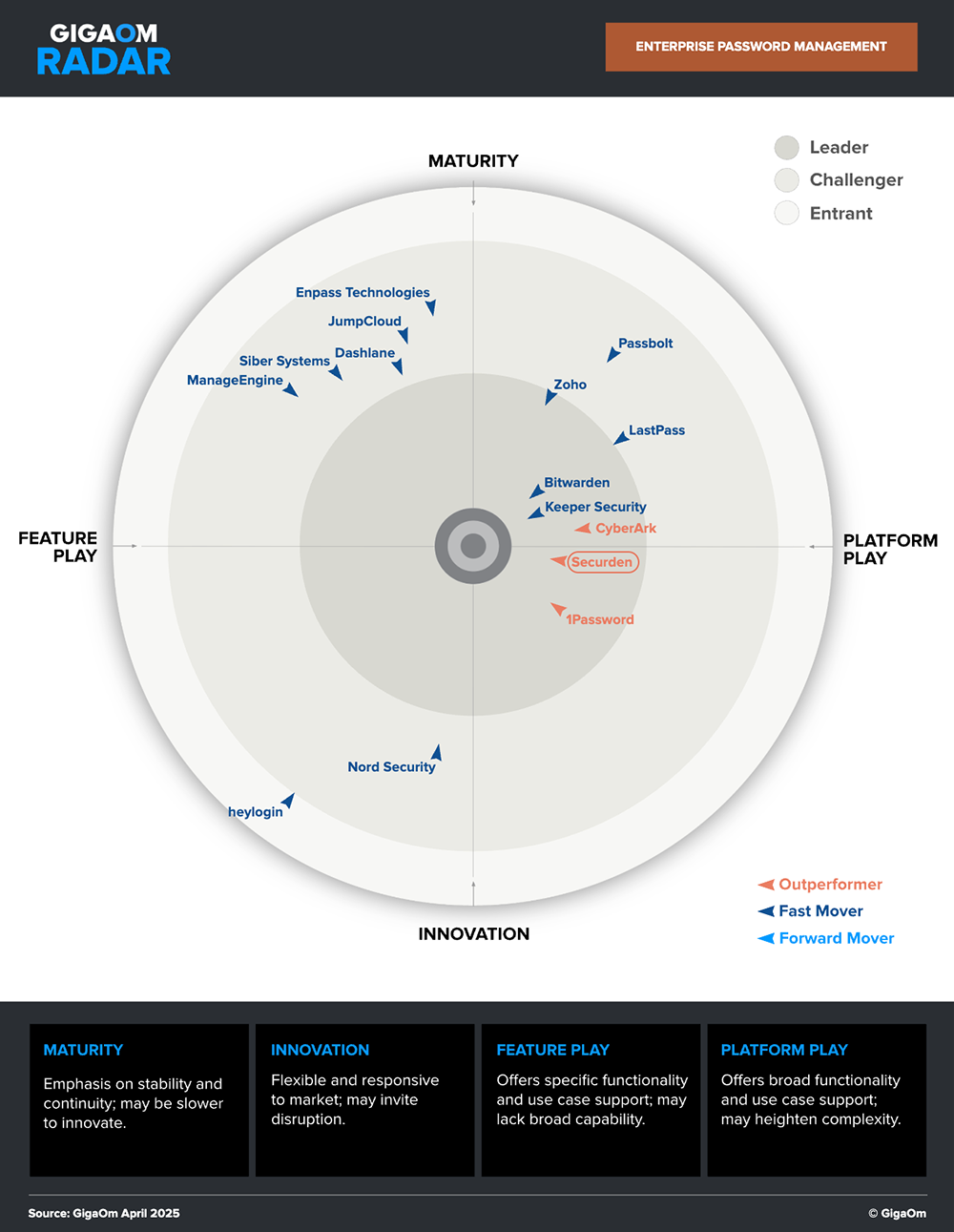
Securden is a market leader and an outperformer in the GigaOm Radar.
Password management is the practice of securely storing, accessing, managing, and protecting passwords to enhance security and privacy across various online accounts and services. A password manager is an application that lets individuals and businesses to efficiently organize all their credentials from a centralized location.
Passwords grow in number as the IT infrastructure of an organization grows. With each new service that the business opts for, and each new website or application that an individual signs up for, the number of credentials increases. With a plethora of passwords to store and maintain, a password manager helps users and organizations simplify their password management challenges. An effective software to manage passwords helps IT admins securely store, share, and manage passwords with centralized visibility and control.
The common threats to password management include login spoofing, sniffing attack, shoulder surfing attack, brute force attack and data breach. These tactics help hackers steal user passwords and earn unlimited access to critical information.
A password management solution helps organizations consolidate and synchronize passwords across all platforms, making it easy to log in wherever you are and on whatever device you use.
Password management helps have provisions to share credentials securely amongst team members. It lets users access accounts without revealing the underlying credentials. A business password manager allows you to control 'who' gets access to 'which' credentials.
Password management solutions let you know if your users are using the same password across all their accounts and notify you if any of the passwords stored are weak and prone to attack. Also, they help rotate passwords frequently.
Password management tools help encrypt passwords and restrict access to sensitive accounts and applications using multifactor authentication (MFA).
Some password management solutions provide advanced functionalities like offline backups and high availability, that prove useful during unanticipated events like server crashes or physical damage to hosted machines.
Purchasing a password management solution is one of the most significant security investments that your organization can make to prevent cyberattacks. Consolidating credentials in a single repository, centralized visibility and accountability, password randomization, automated rotation, and role-based access control workflows help organizations shrink overall attack surface and thwart unauthorized access.
Discover how a password manager can protect your business from cyber threats and streamline credential management.
Cybersecurity can be an unnerving concept for organizations, especially for businesses that don’t have a well-established IT team. However, in today’s digital era, with the internet being the digital silk road for businesses to connect with their customers, hackers are always on the prowl, trying to make the most out of these online transactions. Enforcing simple, easy-to-implement security measures can significantly move the needle on a business’ overall cyber defense. For instance, deploying a password manager that seals gaps in password management, helps establish visibility and accountability, and enforcing credential security best practices can be a powerful first step that businesses can take in their cybersecurity journey. Some key capabilities of a business password management solution are
Complete visibility
Secure password storing and sharing
Password policy
Dark web montoring
Role-based security
Easy user onboarding and offboarding
Complete visibility
Businesses in nascent stages of their growth do not have a dedicated IT team to oversee operations and enforce tight security policies. This leads to employees creating their own passwords on demand as and when required, which are most often strewn around once their purpose is complete. These scattered credentials create backdoors, increasing the number of potential entry points for hackers, thereby increasing the overall attack surface. A clear visibility of 'who' has access to 'what' resources is utmost important, when it comes to identifying and mitigating security risks.
To do so, you'll need robust, easy-to-use solutions that establish good visibility and control, thereby boosting your overall security. A password manager is one such efficient tool. It gives IT administrators complete insights into incoming access requests and what resources and systems are being accessed by organizational users and third-party vendors. It also helps establish accountability over password usage, audit all user activities, and thwart unauthorized access—from a single pane of glass, whether employees work onsite, remotely, or both.
Dark web monitoring
Cybercriminals often target Software as a Service (SaaS) developers and other third-party vendors to gain access to the credentials of their client's employees. A vulnerability somewhere downstream can result in a potential data breach upstream. Millions of such breached credentials are available on the dark web as a dump.
Hackers exploit this information to break into the organizational network, and gain access to sensitive assets. More often, a lot of these credentials are reused which results in malicious actors establishing a strong foothold, breaking into more resources, and expanding their access within the network.
With the dark web monitoring feature, a password management solution can help businesses achieve the following:
Scan the dark web
Notify if any of the passwords your users are using have been previously breached
Provide the list of compromised passwords and measures to replace them with strong and complex ones
Password policy
A lot of users continue to use weak passwords and reuse them across multiple platforms, which is a big threat to organizations. To assist companies in protecting their passwords from cyberattacks, regulatory agencies and security specialists have curated information security standards. Password security is at the core of all these guidelines. Implementing a strong password policy can effectively reduce the chance for cybercriminals to access your data. Password policies help specify password complexity rules, such as password length, accepted/denied characters, a password reset period, and more. Enforcing different password policies for every team in your organization is a security best practice. Password policies can be modified based on the sensitivity of the accounts handled and each team's requirements.
Secure storing and password sharing
Password management tools serve as a repository to store not just passwords but also other sensitive data such as licenses, certificates, agreements, server credentials, private databases, and more.
The good thing is that you can share this information with others in your organization. Password sharing is essential to performing enterprise tasks, but employees need a secure means to share those passwords within their network. This is where a password management solution would help.
Let’s assume that there is a common account that must be used by multiple teams in an organization. In that case, password management tools let you share that account with other groups with different access levels. Business password management solutions also let users manage common folders for specific departments and project teams.
Role-based access control
Every employee should only have access to the credentials they need to perform their jobs. Granting them excess permissions to sensitive data could lead to credential misuse and an increased risk of compromise.
With a password management solution, businesses can adopt Role-Based Access Control (RBAC) which restricts users from having excessive access to resources. Users are provided with access to credentials based on their roles and responsibilities. Controlling network access is important especially when there are a lot of employees and third-party vendors. Companies that have enforced RBAC can better secure their sensitive data and internal systems.
Easy onboarding and offboarding
Onboarding new employees and provisioning access to accounts is seamless when the entire organization uses the same password management solution, even if the whole or part of the team works remotely. With a password manager, provisioning access to the required IT assets can be easily set up, even when there are multiple employees joining at once.
Also, when an employee leaves the organization, access to various resources should be terminated and passwords need to be changed to prevent the ex-employee from logging in. Password management solutions give you visibility on the list of passwords accessed by the departing users and an automated mechanism to change those passwords.
Password attacks are one of the most common types of cyberattacks. A password attack happens when an unauthorized user tries to gain access to an account by attempting to guess the password. Password-related cyberattacks are of varied forms and grow in number by the day. Here are the most common types of password attacks that a password management solution helps defend against.
Brute-force attacks
A brute-force password attack is an outdated method where cyber criminals use trial-and-error techniques to guess the login credentials, secret keys, and other vital data. Hackers employ powerful brute-force password-cracking tools and use them on diverse protocols like software, websites, etc., to crack passwords quickly. If someone has set an easily guessable, commonly used password, it will most likely be deciphered by the hackers in seconds.
Dictionary attacks
Dictionary attacks, a type of brute-force attack, rely on the human habit of using basic dictionary words as passwords. To find a user's password, the hacker attempts every word in a dictionary. Words that relate to your personal info such as your hometown, pet's name, and more are involved in complicated dictionary attacks.
Credential stuffing
If any organization has suffered a data breach in the past, there is a high chance for the breached credentials to be published on the dark web. Credential stuffing is a cyberattack in which cybercriminals use previously stolen credentials to access new accounts or services. This prevails because many people use the same password across different platforms. Hackers would try different combinations of existing usernames and passwords to gain access to new accounts and services.
Password spraying
Password spraying or a password spray attack is also a type of brute-force attack where the hacker tries logging in with the same password to many accounts on the same domain, and if that doesn't work, moves on to the next password. The strength of the user's passwords decides the success of this attack. For instance, if the password is as weak as '123456' or 'abc123', it is likely to be cracked.
Phishing
Phishing attacks occur when a hacker sends you a deceiving link through email, message, or a website with the hopes of getting your personal information. The threat actor collects the data to hack into the user's account with the credentials entered.
Sometimes, it could even be a 'reset your password' link from a phony website or a malicious attachment through an email that impersonates a friend, co-worker, or senior executive in your organization.
Cybercriminals increasingly rely on automation tools to execute malicious activities because they see it as a way to conduct more successful data breaches and gain higher amounts of profit more quickly. Hackers keep evolving their methodologies and it is on the organizations to implement robust cybersecurity tools to defend themselves against these attacks.
Password management can be majorly classified into two types—personal and enterprise password management. While personal password management is about protecting information associated with an individual, enterprise password management aims at securing highly sensitive information and credentials that circulate within an organization.
Personal password management is the practice of storing personal information, such as email accounts, banking details, credit card numbers, social security numbers, phone numbers, contact addresses, and more in a safe vault.
Millions of people use weak or easily guessable passwords to remember them for all their accounts. Families handle multiple shared accounts, from video streaming sites and shopping accounts to banking credentials.
A personal password management solution allows individuals and families to properly organize and share their credentials within and easily manage all their important data from one safe place. While there are many paid password managers, some personal password management tools are also free. People can try out several such versions and pick the one that best matches their purpose.
Enterprise password management is the practice of storing your company's accounts, passwords, and other important credentials in a centralized, secure vault.
One of the most serious threats to your IT security systems is unprotected sharing and misuse of privileged accounts. Various departments within an organization follow different, unsafe ways of storing credentials, such as in a spreadsheet or sticky notes. Enterprise password management solutions reduce the risks associated with compromised credentials by securely storing all the sensitive data in an encrypted vault and by preventing unauthorized access to privileged credentials.
Also, even for a small number of users, managing all their passwords manually is time-consuming and becomes tedious as the organization grows. Using a business password management tool for teams seamlessly manages all the employees' credentials, automates password management operations, and lets them securely exchange passwords across the organization while maintaining total security. Typically, enterprise password management solutions are designed to manage credentials, track and audit important activities, and improve password security for large teams.
A password management solution secures data by letting you store and manage your credentials in a centralized vault. To protect all the data, password management solutions use an encryption, such as the AES-256-bit encryption. To access this encrypted database, you need an encryption key or a master password, which is usually held only by the application administrator. Password management tools help automate password resets during instances of account lockout, eases password sharing among team members, and capture all password-related activities in audit trails. Also, password management solutions eliminate hardcoding through APIs. Hard coding is one of the unsafe programming practices for password storage. Exposure to a single hard-coded credential could put the entire organization at risk. An effective password management solution solves this with a set of secure APIs for application-to-application (A-to-A) and application-to-database (A-to-DB) password management.
A password manager is not the only solution for preventing cyberattacks. But, when coupled with other security software and controls, it becomes an impenetrable line of defense. Password management solution moves organizations from a completely unsafe platform to a stable one by significantly reducing the attack surface. Password managers protect your passwords in a variety of ways. Businesses have so much sensitive data to protect, and they need foolproof encryption to safeguard it. Password manager for business with Advanced Encryption Standard (AES) 256-bit, military-grade encryption store all the credentials in an encrypted form, making it highly impossible to crack, even if it's stored in the cloud.
Many password management solutions have Multi-Factor Authentication (MFA) and additional biometric security measures such as fingerprint scanning or facial recognition. This eliminates the need to enter the encryption key or the master password every time and adds extra layers of security, making your credentials safe.
Password management tools alert you to change your passwords regularly and give periodic notifications on password expiration. Most password management solutions perform a strength assessment where each password is given a strength score based on password complexity. Also, some password management tools have the feature to examine the dark web to see if any of your passwords have been breached already. The passwords can be masked and revealed according to user roles. Moreover, most password management solutions work on zero-knowledge principle, that is, neither the software creator nor anybody else have any knowledge of the data stored, proving to be a safe choice.
Password management solutions are of different types. Businesses or individuals opt for the ones that best suit their needs. The most common types of types of password management solutions used in business domains are self-hosted or on-premise password management solutions and cloud-based password management solutions.
Self-hosted/On-premise password management solutions:
Password management solutions of this kind are chosen mainly by enterprises. Desktop-based password managers allow you to store passwords locally in your environment, on a laptop or desktop, within an encrypted vault. Organizations with an intent to secure their infrastructure i.e., their resources, services, and finances, are generally reluctant towards exposing their internal systems on the internet. Such businesses opt for an on-premise solution. On-prem password management solutions need to be installed on a central server within the organization and act as a standalone application over which you can have complete control. All data can be securely stored and managed in-house. Users can choose to access their credentials even when they are offline in an on-prem solution.
Cloud password management solutions:
Cloud-based password management solutions allow you to store your passwords on the cloud, i.e., service provider's network. Your service provider takes the sole liability for safeguarding all your credentials. The key advantage of cloud-based password manager solutions is that you can use your password manager from anywhere as long as you have an active internet connection. This makes it an appealing choice for both individuals and businesses.
Explore advanced features like centralized visibility, dark web monitoring, and automated password rotation.
Privileged Access Management (PAM) solutions and Enterprise Password Management solutions help businesses meet different levels of security requirements.
Businesses opt for password management solutions when they need to store and organize their passwords and other important credentials in a centralized encrypted vault. Password managers make password management easier for the entire organization, from access provisioning for new users, managing accounts to administrative operations. Compared to PAM solutions, password management solutions are less expensive, and many companies deploy them as the first step to protect their privileged credentials. However, when companies expand, they outgrow the existing tools and the need for more advanced automated processes, auditing mechanisms, and session monitoring capabilities increase. PAM solutions help businesses fill this gap through the following features:
Discovering, controlling, and managing all your privileged accounts and their access to your critical systems, all in one place.
Generating detailed reports and comprehensive audit trails.
Providing secure remote access, remote password reset, session management, and recording.
Restricting the excessive usage and sharing of privileged accounts through the principle of least privilege.
Cybersecurity is a vast landscape and it’s hard to find one solution that can effectively take care of all your organization’s needs. There are multiple factors that one has to consider before investing in an IT security solution. Parameters like organization size, IT team maturity, distribution of PII, budget constraints, compliance requirements help IT admins choose the right kind of solution to meet their requirements.
For example, a password management solution would be a great start if your business has limited IT budget and the main requirement is to have a centralized password inventory and monitor credential usage.
An enterprise-grade password management solution incorporates fine-grained access control workflows depending on user roles and requirements, along with advanced capabilities like automated credential rotation, policy enforcements, and so on.
A privileged access management (PAM) solution on the other hand, helps organizations take complete control over privileged accounts like root accounts, local admin accounts, domain admin accounts, and it helps IT teams establish strict governance over privileged access pathways.
Apart from credential management, there are various facets in the IT ecosystem where security measures have to be implemented and there are multiple solutions available in the market to meet those requirements. And businesses need a combination of one or more of these solutions to seal security loopholes and gain significant visibility and control.
Privileged password management extends beyond human passwords and includes application passwords. These application passwords are often written in plain text within the services they run. Infact, this hardcoding practice is dangerous, resulting in security threats like data breaches, identity theft, system compromise, supply chain attacks, and malware infections. Thus, it is essential to manage them, monitor them, and remove them as organization’s security policies change.
Privileged accounts possess elevated permissions and access to critical systems and data. They pose a significant risk if not managed properly. Below are some types of privileged account password management software helps protecting:
Service accounts: Changing service account passwords needs care since applications depend on them for daily operations. Examples of service accounts include batch jobs, IIS app pools, and windows service accounts.
Domain administration accounts: These accounts help with managing servers and AD users. They also inlcude local domain accounts at the workstation level.
Root accounts: Password management software helps in managing Unix/Linux platforms which are hard to synchronize. They also help in mapping to AD for accountability purposes.
Networking accounts: These accounts enable access to critical infrastructure such as routers, switches, and firewalls.
System admin accounts: These accounts help in managing databases and are often hard to secure and rotate. Being shared with multiple IT administrators who need access to these accounts in real time makes it hard to manage.
Application accounts: Example of application accounts include database logins, certificates for software signing, embedded build script passwords, configuration files, and application services used during software development. Privileged credentials, often hard coded in applications or written in plain text, are easy to exploit.
Password management software helps with securing non-human credentials. Like users, systems like databases, networks, and applications require a password manager to authenticate. These credentials are often not tied to human identities, meaning that accountability is out of the question. Without accountability, the chances of data breaches are even greater. Some examples of non-human identities include databases, applications, networks, APIs, and machine identities (IoT device identities, server identities, virtual machine identities), DevOps tool accounts, and cloud service provider (CSP) accounts.
Any enterprise password management tool should have the following basic features to protect your data and implement effective organizational control.
Centralized management
Password management tools store not just passwords but also encryption keys, documents, and other digital identities, all under a centralized repository.
All the stored data are protected with 256-bit AES encryption.
Administrators gain centralized control and can specify 'who' can have 'what' access to resources.
AD integration, MFA, SSO
Business password management solutions let you integrate your vault with Active Directory services, with which you can securely onboard the employees and provide access to IT resources in minutes.
An enterprise password management solution with Single Sign-On (SSO) integration would let the users authenticate through identity providers (Okta, GSuite, OneLogin, etc.,) to access the password vault. The service provider (i.e., password manager) sends in the required user information to the identity provider, as a request to validate the user.
Multi-Factor Authentication (MFA) is a secondary authentication layer to your encrypted data. Password management tools support many MFA options; you can choose the one most suits your needs.
Password automation
Manually handling the passwords of an enterprise is cumbersome. Immediate notifications on password changes, comprehensive reports, and complete supervision are only possible with a password management solution.
Enterprise password management tool helps with creating strong, unique passwords with a built-in password generator. Also, it helps in randomizing the passwords periodically and do the password reset processes.
Audit and Reports
Most business password management solutions come with an auditing mechanism that maintains a trail of activities (ex: password retrieval, account deletion, etc.) performed by your users.
The audit trails give you a complete overview; you can evaluate, analyze, and determine 'who' did 'what' and 'when.'
Password management solutions also provide comprehensive analytical reports with compelling security insights.
Role-based access control
Business password management solutions employ role-based access control workflows that enable users to only access their accounts and passwords based on their roles. Administrators get to set the level of privileges for each new user added to the password vault.
Users can be given time-limited permissions to access highly privileged credentials. With Just-in-Time access provision, administrators can grant access to any specific password or an application upon requests raised by users.
An enterprise password management solution or a password vault is usually the first, yet significant step that businesses take to manage and secure their passwords. There are multiple parameters that organizations need to look into before deciding to purchase a password management solution. Listed below are a few questions that can get you started on an analysis about your priorities and requirements.
Is it easy to adapt?
How secure is password protection?
What happens in case of a breach?
How does the password management solution ensure only authorized users can access sensitive credentials?
Is it scalable and enterprise ready?
Password management involves auditing all user and account activities and helps enterprise IT teams maintain a clear track record of ‘who’ accessed ‘what’. Furthermore, these audit trails are captured as actionable canned reports that come in handy during various security and forensic audits.
Password management solutions help with not only managing employee passwords but also the passwords of third-party contractors. These vendors require time-limited access to critical assets and their behavior can fully be monitored with password management software.
Further, masked exposure is a common feature found in password management software that lets you share passwords with third parties in a way that minimizes the risk of exposure. For instance, instead of sharing the full password, password management software shares a masked version where some characters are hidden or replaced with symbols. Additionally, another best practice that’s often employed is dynamically changing the masked version of the password over time. This makes it almost impossible for unauthorized users to access actual full passwords.
Ensure secure storage of passwords
Saving passwords in an encrypted vault is a fundamental principle when it comes to password management. Modern password management solutions come with AES-256 Bit encryption, in that attackers can’t view passwords even when the vault is accessed. Some potential benefits of using a password management system include convenience, efficiency, and security.
Adopt a password manager
Utilize a password manager to streamline the entire password lifecycle – creation, updating, and sharing. Password managers allow IT administrators to track password activity, ultimately helping businesses meet compliance standards.
Use strong, unique passwords
Using short, simple, and easily guessable passwords across multiple accounts makes it easier for hackers to exploit your sensitive data. Use strong and complex passwords that are tough to crack and rotate periodically for secured protection.
Randomize passwords at regular intervals
Enforcing frequent password rotation prevents the reuse of old passwords and restricts the possibility of multiple accounts being breached. Most organizations follow certain regulations or have a password rotation policy with which it provides specific recommendations for password rotation. The frequency of password rotation varies depending on the account type, value, and usage. Passwords of privileged accounts might require a more frequent rotation, while that of the standard user accounts might require a rotation once in 30 or 60 days.
Implement multi-factor authentication
Apart from the standard security measures, enforce a second layer of authentication at all levels. Multi-factor authentication (MFA) can effectively restrict unauthorized access through two successive layers of authentication, ensuring that an authorized user is who they claim to be. Organizations need MFA to protect their systems, network, and data, and to defend themselves against various cybercrimes.
Check for compromised credentials
Review password usage across your organization regularly, and check if any of your passwords match with the breached credentials database available on the dark web.
Enforce principle of least privilege
Not all users should have complete access to all the data present in your organization. Access should be solely granted based on the users’ role and responsibilities, so they only have the necessary privileges to perform their tasks.
Continuously track audit trails
Repeated login attempts and the frequency of password reset requests are two key factors that should be examined often. Unusual trends in these actions could indicate a sign of password exploitation.
To accrue the full advantage of a password management system, it's crucial to follow best practices for implementing and maintaining.
#1 Pick the most convenient password manager
Choose a password manager that’s ideal for your org size, the level of customization required, and preferred hosting criteria (self-hosted or cloud-based). While evaluating a password management system, carefully assess the security features, scalability, ease of use, and cost.
#2 Educate your internal users
User training is important for successful adoption of password management software. All users must realize the importance of password security, get a solid understanding of company password policy, and understand how to best use the password manager.
#3 Regularly update the password policy
As businesses evolve, their password policies should also follow suit. Constantly alter password policies to meet your needs.
#4 Integrate with your existing tech stack
While implementing a password management system, ensure it integrates well with your infrastructure. From SSO and browser extensions to custom integrations, make sure it checks all the boxes.
#5 Have a thorough backup plan
Modern password management systems come with holistic backup and disaster recovery functionalities. Have a regular cadence of backing up password management’s data. The backups should be encrypted to safeguard underlying credentials. This will come in handy during hardware failures, accidental deletions, unforeseen circumstances. Also, devise a plan to restore data from backups to prevent further damage in the wake of data breach.
#6 Avail yourself of ongoing maintenance and support
Update the password management system regularly to benefit from advanced security patches, feature enhancements, and bug fixes.
Deploying a password management system helps various participants within a company. For instance, it helps C-level executives, IT teams, and employees. Password management systems help ease the work of everyone – more secure and more convenient – all at the same time.
#1 How do password management solutions empower C-level executives?
C-level executives get the realization that their employees and IT teams follow cybersecurity and password management best practices. They protect themselves and the organization they are building while managing and securely sharing credentials. Overall, C-level executives give buy-in to the password management software that has been collectively chosen by their IT teams and employees.
#2 How do password management solutions empower IT teams?
A password management solution empowers IT teams by addressing key challenges in cybersecurity, operational efficiency, and compliance. It enhances security by enforcing strong password policies and Multi-Factor Authentication (MFA), reducing the risk of credential theft and data breaches. Centralized visibility into employee password behavior helps IT identify vulnerabilities and enforce best practices.
Further, password management solutions improve operational efficiency by reducing help desk requests for password resets, allowing IT teams to focus on strategic initiatives. Features like self-service password resets and synchronization across applications streamline workflows. Secure sharing of credentials enhances collaboration among team members without compromising security. Role-based access control ensures employees have access only to necessary resources, aligning with the principle of least privilege. Advanced features such as encryption and integration with tools like Single Sign-On (SSO) further enhance both security and usability for IT teams.
#3 How do password management solutions empower employees?
Password management solutions empower employees by simplifying their daily workflows and enhancing security. These tools allow employees to securely store, manage, and share passwords in a centralized vault, eliminating the need to remember multiple credentials or rely on insecure practices like password reuse. Features such as automated password generation and encrypted sharing streamline collaboration while ensuring sensitive information remains protected. Employees also benefit from reduced frustration caused by frequent password resets, which improves productivity and minimizes disruptions.
Additionally, password managers help employees adopt strong security habits, such as creating complex passwords and using Multi-Factor Authentication (MFA). By integrating seamlessly across devices and platforms, these solutions make secure practices more convenient, encouraging employees to use them both professionally and personally. Employees appreciate the ease of access to their accounts while knowing their data is safeguarded against cyber threats.
Don’t let weak passwords put your data at risk. Secure your credentials with military-grade encryption and MFA.
Better password management starts with setting policies and effective shelf life and enabling single-sign-on (SSO), and multi-factor authentication. With SSO, users get seamless login experience and with multi-factor authentication, users can expect increased security. These aspects together shape and give rise to innovative (better) password management. Also, the future of password management includes a combination of the following:
Passwordless logins - Passwordless login methods like biometric are likely to emerge.
Passkeys - Passkeys using public key cryptography and biometric authentication will replace text-based passwords.
Zero-knowledge encryption - With zero knowledge encryption, the service provider will not be able to decipher user's stored password.
Multi-factor authentication - With MFA, users need to go through two sets of evidence to access accounts.
Cross-platform integration - Password managers integrate with multiple devices and platforms, helping users access passwords from anywhere.
Purchasing and deploying a password management solution is a crucial step organizations need to take to secure and regulate access to sensitive information. Securden Password Manager for Enterprises helps organizations enforce password security best practices by automating password rotation, breached password identification (dark web monitoring), and tracking of password usage. You can generate strong unique passwords in compliance with set policies using the inbuilt password generator.
With tight approval workflows and just-in-time access provisions, you can restrict 'who' has access to 'what' and 'when'. Securden tracks all the password-related activities and provides actionable reports with detailed insights.



Password rotation refers to the practice of periodically resetting password credentials and replacing them with strong, unique passwords depending on policy requirements. Reducing the password reset period limits the exposure to password-based attacks.


Privileged passwords are a subset of credentials in your IT ecosystem that grant elevated access to sensitive accounts, applications, and networks. These passwords protect a range of privileged accounts like root accounts in Linux, local admin accounts, domain admin accounts, service accounts, application accounts etc., that provide access to sensitive corporate data and entitlements.


A one-time password is a temporarily generated password/code that the user can use only once for a specific period of time, after which the code expires.


Privileged password management is the practice of securely storing and managing the usage of specific types of credentials that grant elevated access to sensitive accounts within your enterprise network. Privileged passwords protect critical accounts like root accounts in Linux, domain admin accounts, service accounts, application accounts, database accounts, local admin accounts for systems and network devices and the like.


Enterprise password manager is a tool that stores corporate data like shared accounts and passwords, important keys, tokens etc., in a centralized, secure vault. It reduces the risks associated with compromised credentials by securely storing all the sensitive data in an encrypted vault. Furthermore, enterprise password managers entail strong access control workflows and audit engines that help thwart unauthorized access and improve password security for large teams.


Password managers can majorly be classified into two types - personal and business password managers. While personal password managers protect information associated with an individual, enterprise password managers aim to secure passwords used in a shared corporate environment and passwords of accounts that are not tied to any particular user.


Yes, password managers are the most secure means of protecting passwords. Password managers use AES 256-bit encryption that stores all the credentials in an encrypted form, making it highly impossible to crack.
Moreover, most password managers work on the zero-knowledge principle; that is, neither the software creator nor anybody else knows the data stored, proving to be a safe choice.
Password managers help mask passwords and reveal them according to user roles. It checks if any of your passwords are in the breached credentials database, alerts you to change your passwords regularly, and gives periodic notifications on password expiration. Additionally, password managers integrate with various MFA systems and prompt you to have a second layer of authentication, thus levelling up your overall security.


A password policy refers to the rules and standards for setting up new passwords and determines if the new password adheres with the set complexity requirements. Some of the complexity requirements include password length, password lifetime, password rotation period, accepted/denied characters, and more.


Multi-factor authentication is an identity verification method that requests users to provide two or more authentication factors to verify their identity, for gaining access to various resources. Logging in just with usernames and passwords might lead to security breaches, as anyone with these credentials can quickly get illegitimate access to accounts. MFA builds a layered defense that makes it difficult for hackers to gain access. The secondary authentication factor includes Mail OTPs, TOTPs, Yubikeys, and more. Whenever a user signs into an account with MFA controls, credibility is assessed through one of these different factors, apart from the primary authentication factor–usernames and passwords.


Cloud password managers store passwords on the cloud, on the service provider’s network. They can be deployed instantly without the need for any infrastructure. It lets users access the vault from anywhere and at any time as long as there is an active internet connection. Modern cloud password managers are on-par with on-prem password managers and posses enterprise-grade capabilities such as high availability, database backups and more.


Single Sign-On (SSO) is an authentication technique that lets your users log in to various applications using a single set of credentials. The SSO provider verifies the user identity only once, with which the user gains access to multiple other applications, without needing any further authentication. SSOs are highly preferred in businesses because users consider them a simple and safe way to access applications in one go. It helps consolidate passwords on all related platforms and reduces the time IT spends troubleshooting password-related issues.


Deploying a business password manager can highly improve a company’s cyber defense. With an enterprise password manager, businesses can increase visibility over their employees’ access to passwords and other sensitive credentials. Password managers help enforce role-based access control, set periodic password rotation, and ease employee onboarding and off boarding. Also, they can automate the entire password management practices, instigate password policies, and constantly monitor the dark web to check if any breached credentials are actively used within the corporate environment.


Password generators create strong, complex, and unique passwords for each of your accounts that adhere with your corporate password policy mandates. With advanced algorithms, these password generators use a combination of letters, numbers, and special characters to generate random passwords every time, making it difficult for malicious outsiders and insiders to crack them via brute force attacks.


Privileged accounts such as the application-to-application accounts or machine-to-machine accounts require privileged credentials to access specific applications for everyday operations. The applications will request the credentials to log in, and if it meets the requirements, the associated application, server, or database will authenticate and permit the request. To automate this process, APIs (Application Programming Interfaces) are used.
Through application management using APIs, users can store credentials in a central password vault or management solution instead of embedding them in configuration files or scripts. Incorporating application password management solutions eliminates the practice of hardcoding (storing credentials in an unencrypted form) and prevents breaches due to exposed application credentials.


Password attack is a common type of cyberattack employed by hackers to gain access to sensitive passwords/credentials through unauthorised user accounts. Attackers quickly guess or crack passwords using specific automated tools, revealing users' identities in exchange for a ransom.


To prevent password attacks, organizations should first comprehend the ways and techniques that cybercriminals use to compromise or hack passwords. Businesses can significantly reduce password attacks when they implement defense strategies such as:


There are 8 common types of password attacks. They are:


Password security guidelines help businesses bolster its security and prevent data breaches. Some of the widely incorporated information security guidelines by businesses are:
To know more about the regulations and the password management best practices, visit https://www.securden.com/blog/top-10-password-policies.html


Password management best practices help businesses effectively shield against cyberattacks. Some significant best practices for password management include:


Password mismanagement is the improper handling or misuse of passwords when password management best practices are not followed effectively. This may lead to serious security repercussions including identity theft, phishing attacks, ransomware, and more.


Password mismanagement can be prevented by enforcing and following password management best practices and having a password manager in place. With a password manager, all activities related to password management (password creation and storage, password rotation, checking the dark web monitoring for breached passwords, and more) can be automated and completely monitored. Thus, any human error that results in improper password management can be avoided.


A shared account is used by multiple users in an organization to access applications, servers, sensitive data, assets, and more. This means the same set of credentials will be used to authenticate multiple users, and that no single shared account is linked to a specific user. This lack of accountability could also add up to the security risks that shared accounts hold. Organizations can manage their shared accounts and users by implementing security tools like password managers and privileged access management solutions.


DevOps password management is securing and managing authentication credentials such as passwords, API keys, digital certificates, SSH keys, etc., that are used in DevOps, CI/CD pipelines, databases, servers, and more. A password manager helps consolidate all these sensitive credentials in a central vault, automate password management operations, and track all access to these data.


The price of a password manager varies depending on a number of factors, such as the size of the team, the plans chosen (starter, business, MSP, etc.), and the amount of users and administrators licensed. The feature sets and the duration of the license renewal are additional factors that are taken into account while pricing a password manager.


A secure password manager possesses the following features:


While password managers can be hacked at times, such occurrences can be nullified and made fruitless with the help of multi-factor authentication (MFA), the use of strong master passwords and advanced encryption. Even in the rise of such circumstances, your sensitive information wouldn’t be compromised. That means the attacker can access only encrypted data and would typically have no access to your passwords in clear text.


Password management software helps businesses store and manage their passwords from a secure, centralized location. It eliminates the need for remembering multiple passwords. Most of the password management solutions are accessible from various platforms and devices.
Modern password management softwares use advanced encryption like AES-256, ensuring security. It enables team collaboration and enhances productivity through secure sharing of passwords. Moreover, it offers detailed audit reports on who has access to what and who performed what, tying actions to specific users.


Password management in cybersecurity encompasses a set of security principles and best practices applied throughout the password life cycle from creation to closure. It helps curb unauthorized access with the help of password managers utilizing advanced encryption.


You need to evaluate whether the password management software you’re picking up meets the following criteria:
