Case 1: Application Elevation
Enabling standard users to run specific applications that would normally require administrator rights
Assume that a user in your department would usually run a list of applications and processes requiring administrator rights to install, run, and update. When local administrator rights are removed, and the user is made a standard user, the applications cannot be run.
Securden enables the user (with just standard user rights) to run all those applications without any hassles.
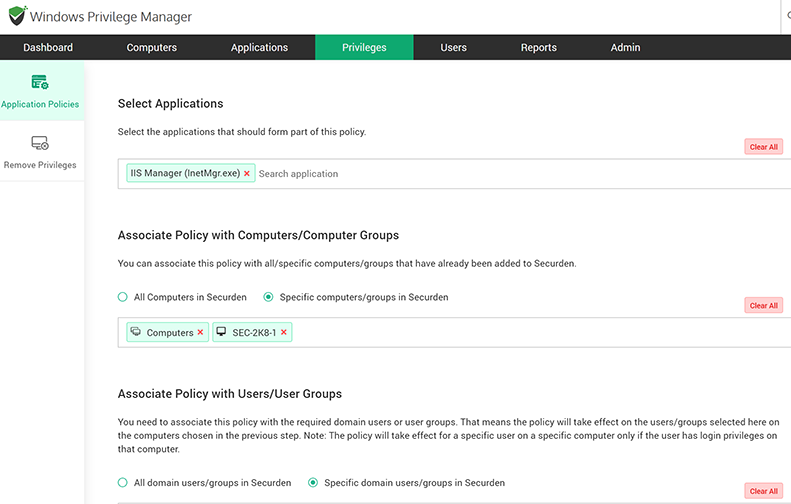
Securden administrator can create a policy marking the list of applications as trusted and permit the user to run those applications on a specific computer or multiple computers. The Securden agent installed on the end-user machine elevates the applications for that standard user.
The user can use/run the applications in one of four ways:
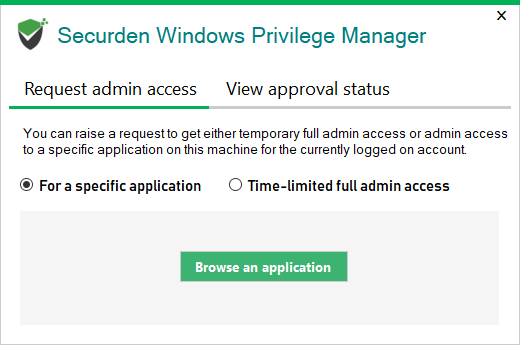
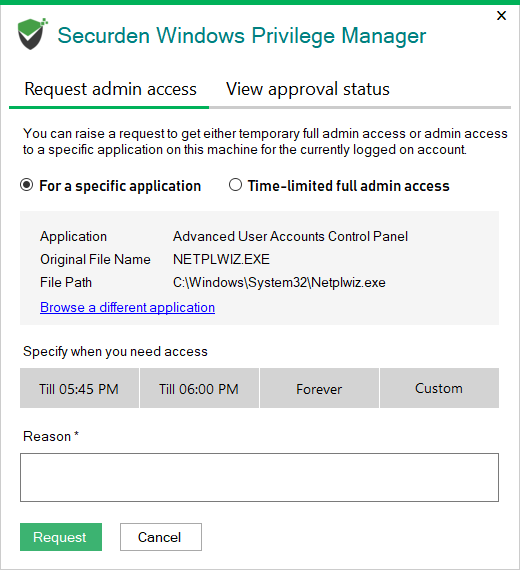
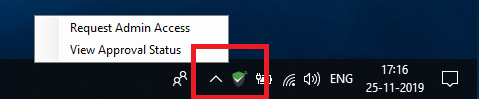
- Double-clicking the Application (Users with admin privileges can double-click and directly open the application.) Users who do not have admin privileges will be given the option to request access - either to a specific application, or temporary full admin access.
- Clicking Run as Administrator (This opens up the UAC prompt, and a Securden dialog will pop up alongside the UAC prompt.
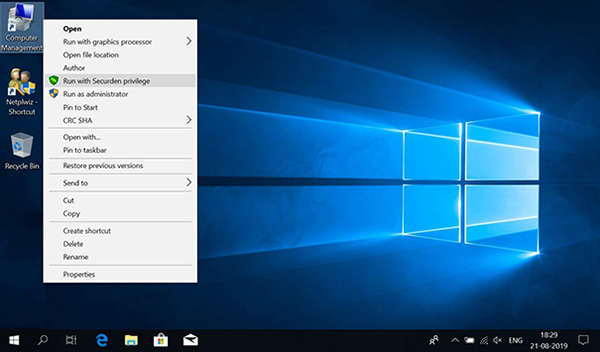
- From the Context Menu (Right-click the application and ‘Run with Securden privilege’) Using this dialog, users can elevate privileges.) This lets users run the selected application based on control policies defined by the administrator.
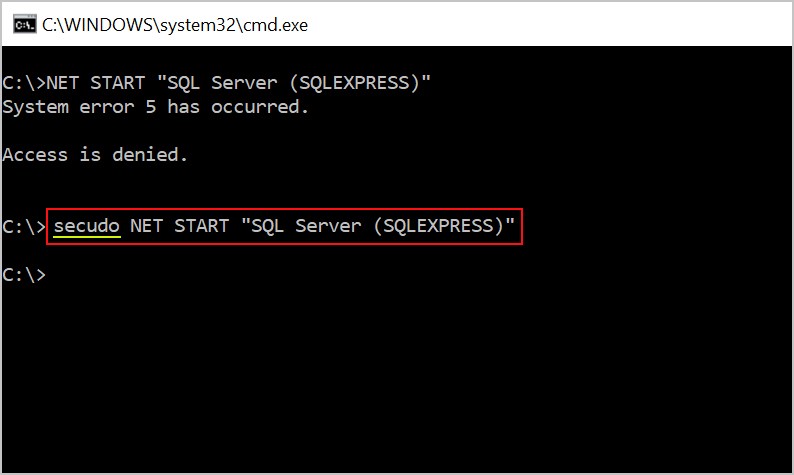
- Using Run Command (Command Prompt with prefixing the word ‘secudo’)
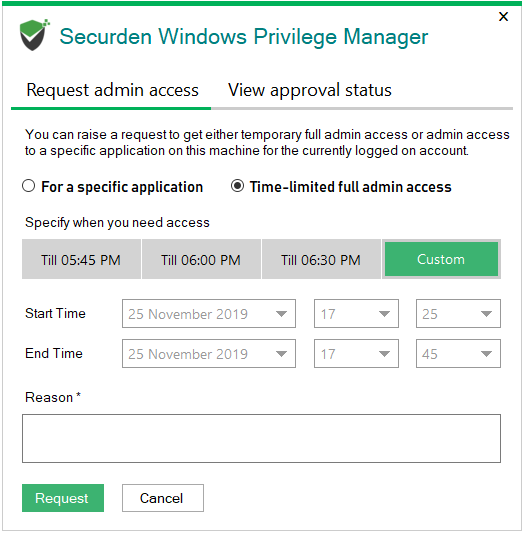
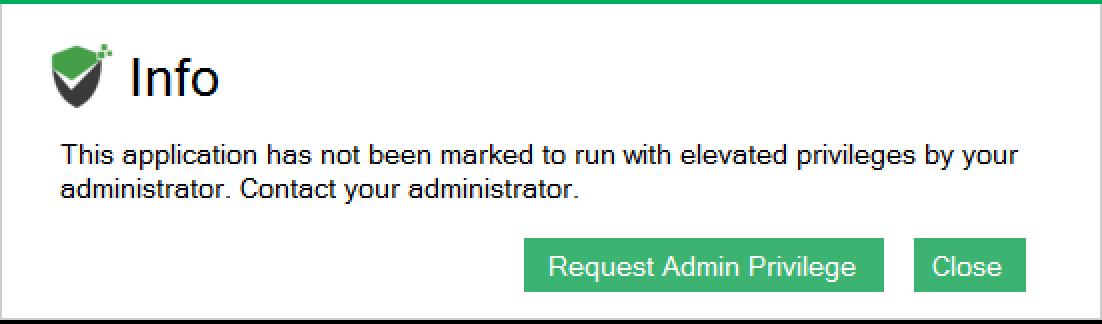
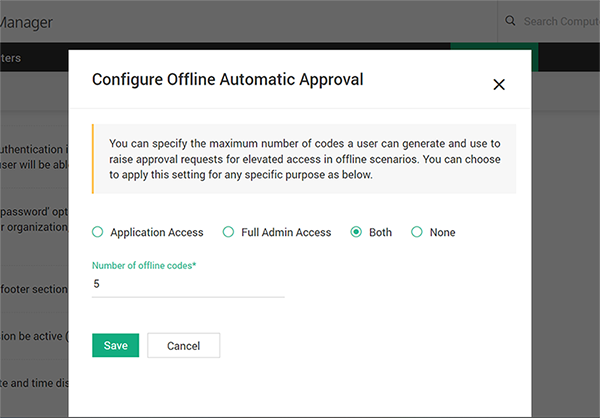
The elevation of privileges is based on the control policies in place. If a policy does not exist for the application, the user can place a privilege elevation request and access the application on approval.
While local administrator rights stand removed, user experience is not compromised, and productivity is not impacted.