The solution runs on a central server connected to a backend database. It comes with an inbuilt web server and PostgreSQL as the RDBMS. Optionally, you can use MS SQL Server as the backend database. The server handles the application control policies. Typically, the policies define the list of trusted applications and who can use/run them.
On the end-user machines, a light-weight agent has to be installed. The agent communicates with the server periodically and gets the policies. The agent takes care of enforcing the policies. The agent can also discover the applications from end-user machines and list them on Securden applications inventory. This would come in handy to create policies.
Typically, the agent tries to get the latest policy from the server when a standard user attempts to run an application. If the agent is not able to communicate with the server, it enforces the policy that was last pulled by it from the server. The product can be deployed in high availability mode with redundant servers. Agents can be pushed to the endpoints in two ways: Either directly from the GUI or through Group Policy Objects.
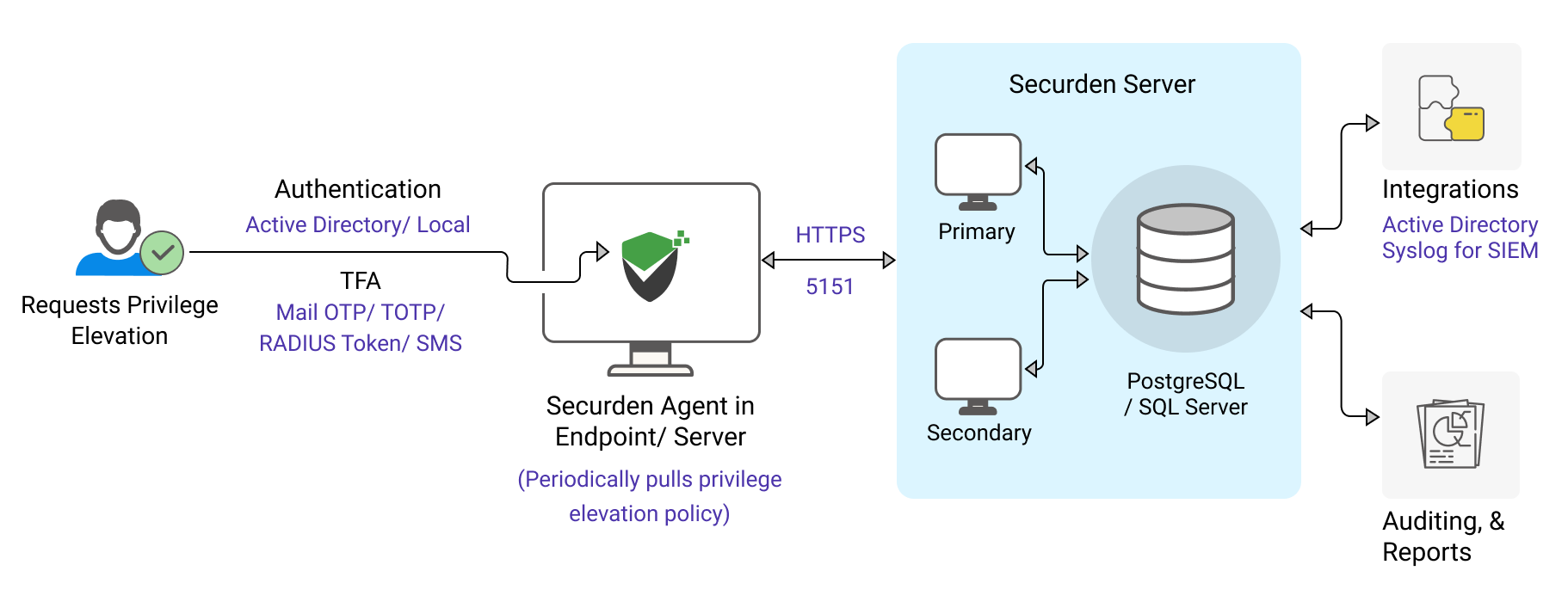
Enterprise requirements such as data backup, high availability, and disaster recovery are in-built. The product integrates with Active Directory for user management and authentication. It also integrates with a variety of MFA providers - any TOTP authenticator (Google authenticator or Microsoft authentication), any RADIUS-based authentication mechanism (RSA SecurID, Digipass, etc.), Duo Security, Yubikey, Email to SMS gateway and OTP through email.
All these functionalities are delivered on a single installation. An installation instance can just have one physical server or multiple application servers as required.
The database columns are encrypted (AES-256) and the database is designed as strictly access controlled. Every installation is guarded by a unique encryption key.
