I greatly appreciate the simple setup of Securden Privileged Account Manager (PAM), which has allowed us to get started quickly and efficiently. I particularly like the excellent ability to securely share secrets and account data between different teams.
Securely Share Admin Accounts
Shared accounts employ a single credential to authenticate multiple users. While this largely goes against IT security best practices, smaller organizations may still make use of shared admin passwords/accounts.
Shared admin accounts decrease the management overhead by reducing the privileged access footprints within your IT estate. However, they come along with risks that need to be carefully managed.
What are the Challenges Associated with Shared Admin Accounts?
Since they are shared among many people across teams and departments, they need constant monitoring to ensure access is always restricted to the right set of people for the right reasons at any given point in time. Any lapses here could lead to unauthorized access as well as opening up vulnerabilities for the hackers to exploit.
Producing a clean audit trail is a challenge as the logs will only show the shared username. There is no direct way of tying up each action against the individuals. This could lead to accountability issues.
How PAM Solution Aids in Overcoming Admin Account Challenges?
Shared accounts must be managed like any other highly privileged account, and must be used in combination with Unified PAM.
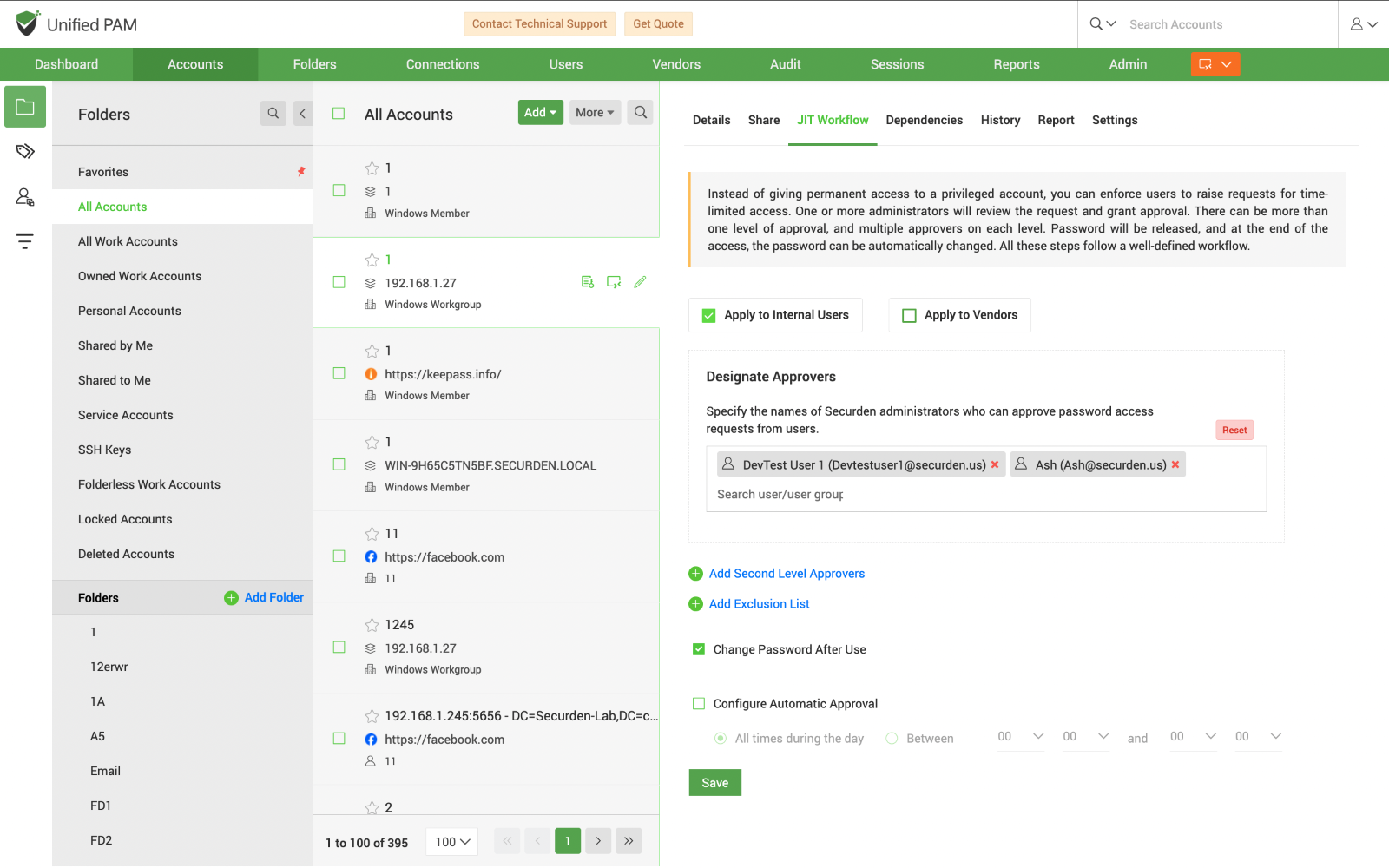
- PAM brings in Session monitoring and recording capabilities along with audit log features. This allows you to map the actions against individuals using the shared account ensuring accountability which otherwise would be difficult to achieve when multiple users share the same account.
- Passwords of privileged admin accounts can also be periodically rotated after a user has accessed them, ensuring that they cannot remember the credentials and carry out unauthorized access.
- Multi-factor Authentication (2FA) can be enforced for all privileged admin accounts in PAM, ensuring that only authorized users can access them.
- IT can grant time-limited (JIT) access to admin accounts ensuring that the user is given enough time to complete their tasks.
Just like any other privileged account, you need to enforce robust automated password management features to shared admin accounts as well. PAM's continuous monitoring and controlling features along with the audit logs helps you to stay on top of all your privileged activities done using a shared admin account.