I had a great experience with Securden. It provided me a way to unify saving passwords across my different environments (on-prem and in the cloud)
How many Privileged accounts does your IT environment have?
Most enterprises possess a shedload of devices, where hundreds of accounts reside inside each of them. It is humanly impossible to have a record of the number and type of accounts. Among these accounts, only some are known and used on a regular basis, while the others are unnoticed and orphaned. Manually tracking them is an arduous and error-prone task. Consolidating and managing them becomes simple with an automated privileged accounts discovery process.
To obtain a comprehensive picture organization-wide, consolidating the accounts under a centralized vault is essential. Securden aids the fundamental step of consolidation with a robust discovery engine that fetches the accounts in servers, databases, and network devices to develop a roster for organized management.
Discovering & consolidating accounts: Critical for visibility
To obtain a comprehensive picture organization-wide, consolidating the accounts under a centralized vault is essential. Securden aids the fundamental step of consolidation with a robust discovery engine that fetches the accounts in servers, databases, and network devices to develop a roster for organized management.
Why dormant accounts pose grave threats
Unmanaged accounts always pose significant security threats. There could be scenarios where many accounts might remain dormant, and administrators might not even be aware of their existence. Following are some typical scenarios:
- Privileged accounts of users who bid adieu to the organization
- Shadow IT accounts created by employees & developers
- Accounts that were not deprovisioned after offboarding a third-party contractor or a vendor.
- Long-lost Privileged Accounts
- Unmonitored Device Accounts
- Accounts created for testing purposes .
- Hidden backdoor accounts, which are used to steal sensitive data
All such accounts should be brought under control and management. But that requires visibility into their existence in the first place. Privileged accounts discovery precisely uncovers all dormant accounts so they can be managed by the IT administrator.
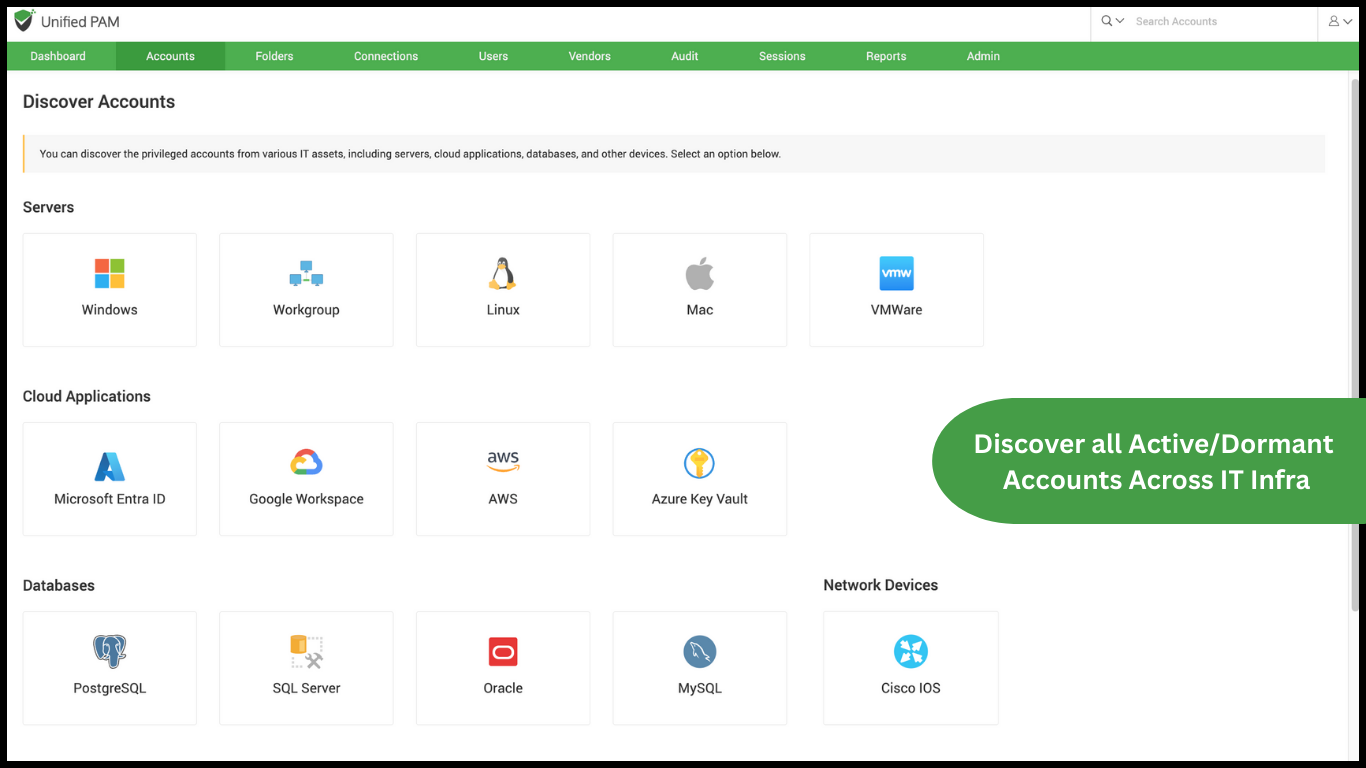
Track down all critical IT accounts and take charge
Securden scans your network, discovers devices and all accounts therein, including dormant accounts, and consolidates them for efficient administration. The different types of accounts discovered include:
1. Server Accounts:
- Windows accounts (local, domain, and dependent service accounts)
- Linux devices and their accounts
- Mac devices and the accounts, devices and the accounts thereof
2. Database Accounts
- Accounts associated with Microsoft SQL Server, Oracle, MySQL, and PostgreSQL databases.
3. Cloud Infrastructure Accounts
- Accounts and keys distributed across Azure (Microsoft Entra ID), Google Workspace, AWS Cloud, and Azure Key Vault.
4. Network Devices:
- Accounts associated with various network devices such as switches, routers, firewalls, and other network devices from various vendors such as Cisco, Juniper, HP, etc.
5. Virtual Accounts
- Accounts present across your virtual infrastructure. Those present in VMWare ESXi hosts and Virtual Windows, Mac machines.
6. Other Accounts
- Active Directory and LDAP-compliant directory services account
- Privileged accounts used in web services such as ASP.NET config files and SharePoint; and in middleware tiers such as Oracle WebLogic, IBM
- Privileged accounts used in web services such as ASP.NET config files and SharePoint; and in middleware tiers such as Oracle WebLogic, IBM WebSphere, and SAP NetWeave.
- Cloud identities on platforms including Office 365, Azure Active Directory, Amazon AWS, IBM SoftLayer, Rackspace, and Force.com
Strengthen security by rotating passwords upon discovery
When consolidating passwords from various sources, it is important to ensure that the existing passwords are changed with randomly generated strong, unique ones. This action annuls the passwords accumulated in spreadsheets and text files and offers a fresh start to Privileged Access Management.


